Pirate,
Email spam is once again the most popular choice for sending out malware. Spam has been one of the main infection vectors for decades. During the past few years, it’s gained more popularity against other vectors, as systems are getting more secure against software exploits and vulnerabilities. A recent report of F-Secure reports that spam email click rates have gone up from the 13.4% recorded in the second half of 2017 to 14.2% recorded in the first half of the year. To protect against these attack vectors is nearly impossible as a majority of attacks leads to web pages never seen before and due to the the sheer infinite range of these attack vectors. The only thing that really improves our security level is permanent education of our users.
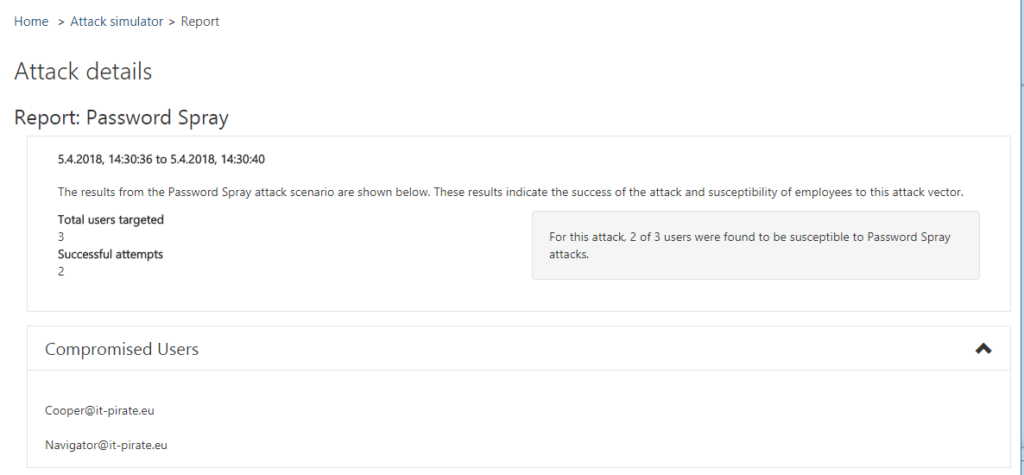
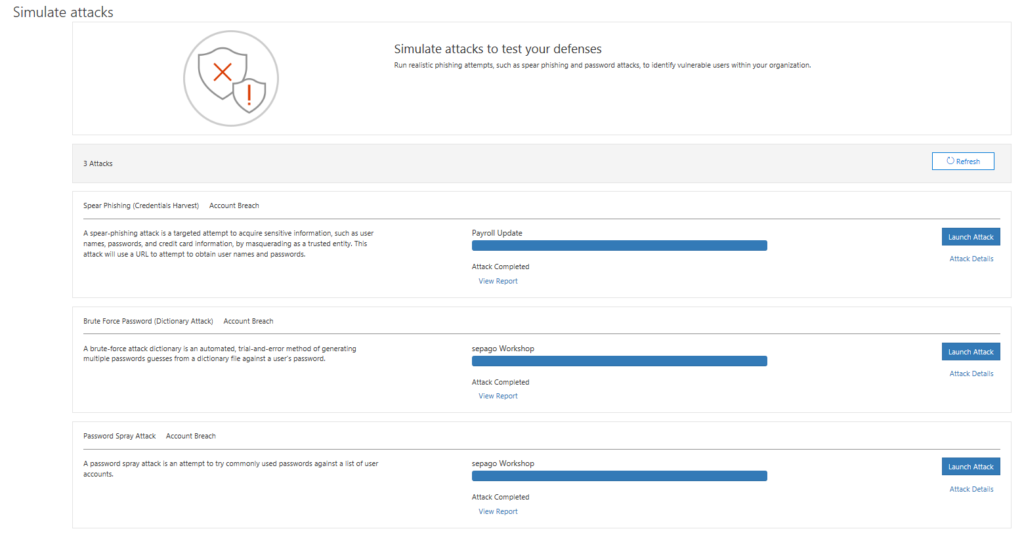
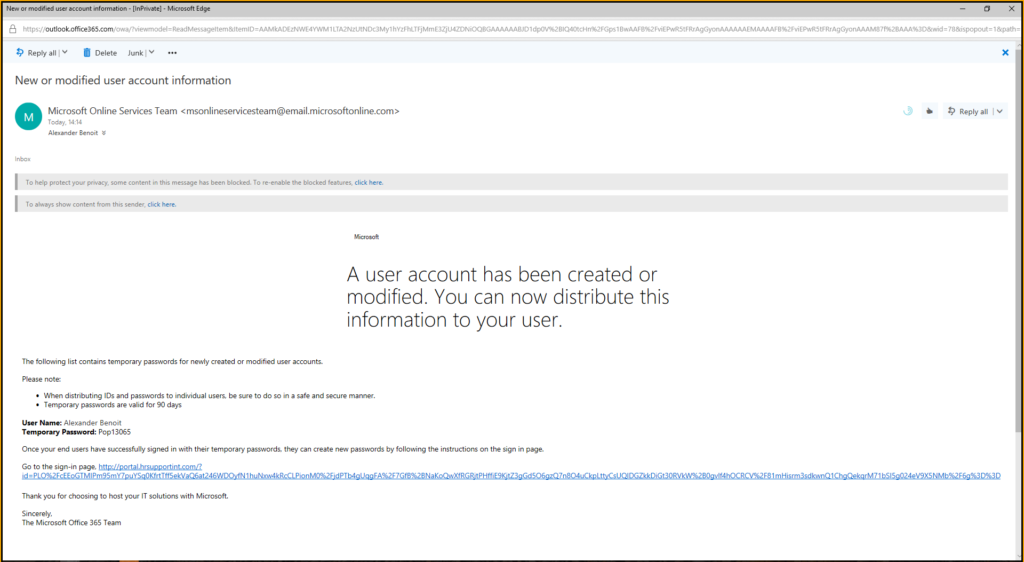
On 02-21-2018 Microsoft has announced the Public Preview of Attack Simulator for Office 365 Threat Intelligence. In preparation of some customer workshops I had a first look into the product that I want to share with you.
Continue reading