Pirate,
A Brute Force Attack is the simplest method to gain access to a site or server. It is an automated, trial-and-error method of generating multiple password guesses from a dictionary file against a user’s password. Automated software is used to generate a large number of consecutive guesses as to the value of the desired data. An attack of this nature can be time- and resource-consuming. Hence the name “brute force attack;” success is usually based on computing power and the number of combinations tried rather than an ingenious algorithm.
This is the third part of the Attack Simulator for Office 365 Threat Intelligence series:
- Attack Simulator for Office 365 Threat Intelligence – Overview and Preparation
- Attack Simulator for Office 365 Threat Intelligence – Spear Phishing attack
- Attack Simulator for Office 365 Threat Intelligence – Brute Force Password
- Attack Simulator for Office 365 Threat Intelligence – Password Spray Attack
Brute-force attack when an attacker uses a set of predefined values to attack a target and analyze the response until he succeeds. Success depends on the set of predefined values. If it is larger, it will take more time, but there is better probability of success. The most common and easiest to understand example of the brute-force attack is the dictionary attack to crack the password. In this, attacker uses a password dictionary that contains millions of words that can be used as a password. Then the attacker tries these passwords one by one for authentication. If this dictionary contains the correct password, attacker will succeed.
In traditional brute-force attack, attacker just tries the combination of letters and numbers to generate password sequentially. However, this traditional technique will take longer when the password is long enough. These attacks can take several minutes to several hours or several years depending on the system used and length of password.
Give the attack a random name.

…select the user on which you want to affect the attack

Now you can enter the passwords that you want to proof or you can add a password dictionary list. You can find password lists everywhere in the internet. For demo’s I often take the lists from this github repository.

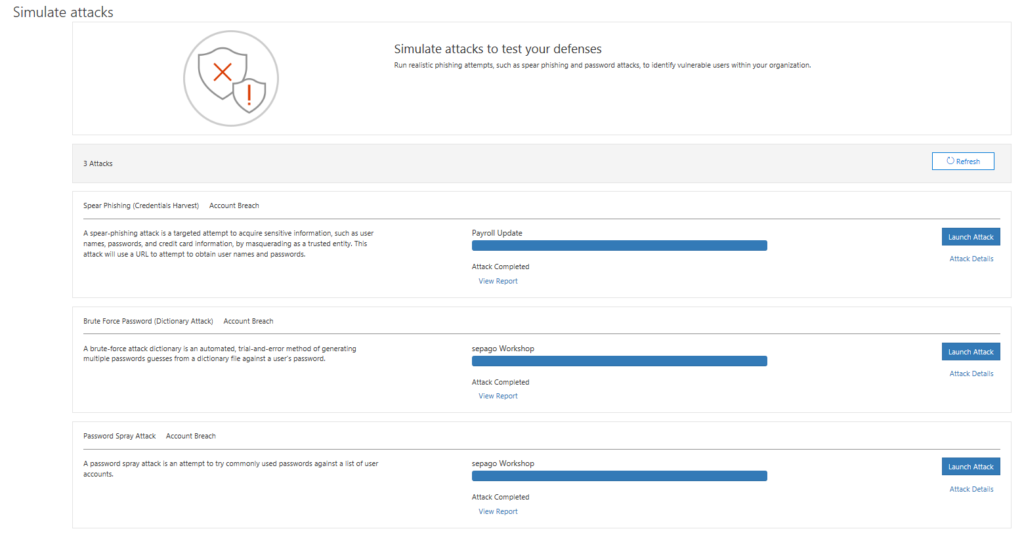
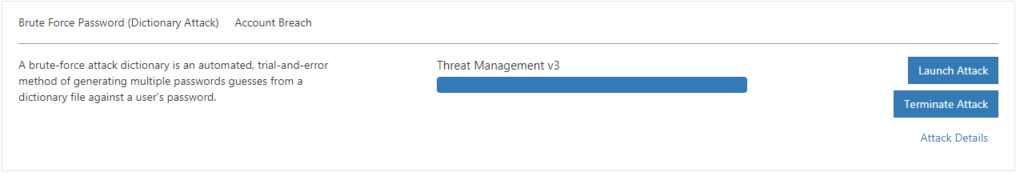
If you then launch the attack you can see the status of it in the simulate attacks overview.
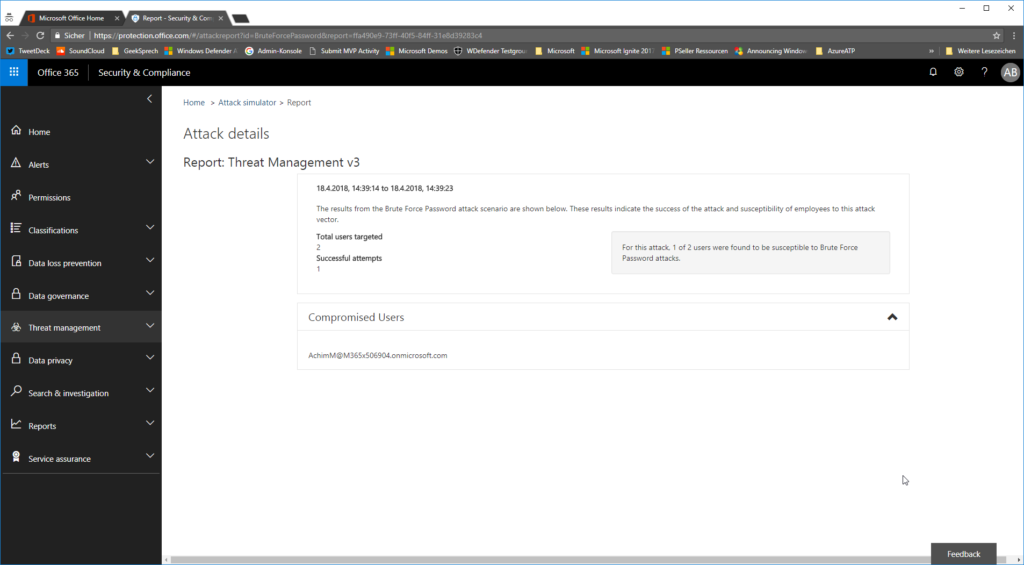
If you click into the attack details you will find the users that got compromised by any of the parameters.
Check out the last part of the series which is: the password spray attack.
Have fun!
*Cpt
References:
Attack Simulator in Office 365

Submit a comment on “Attack Simulator for Office 365 Threat Intelligence – Brute Force Password Attack”