Pirate,
in the first part we had a look into attack simulator and the included scenarios. We discussed which scenario does what in detail and what you need to set up as a preparation. In this blog post we will check out the spear phishing attack that is meant to harvest credentials. Spear phishing is a very common e-mail spoofing attack scenario that targets a specific individual or organization with the goal to get access to sensitive information. Furthermore I have seen this attack method with the intend to install malware on a targeted user’s computer.

This is the second part of the Attack Simulator for Office 365 Threat Intelligence series:
- Attack Simulator for Office 365 Threat Intelligence – Overview and Preparation
- Attack Simulator for Office 365 Threat Intelligence – Spear Phishing attack
- Attack Simulator for Office 365 Threat Intelligence – Brute Force Password
- Attack Simulator for Office 365 Threat Intelligence – Password Spray Attack
Navigate to https://protection.office.com/ and click on Threat Management > Attack Simulator > Launch Atack
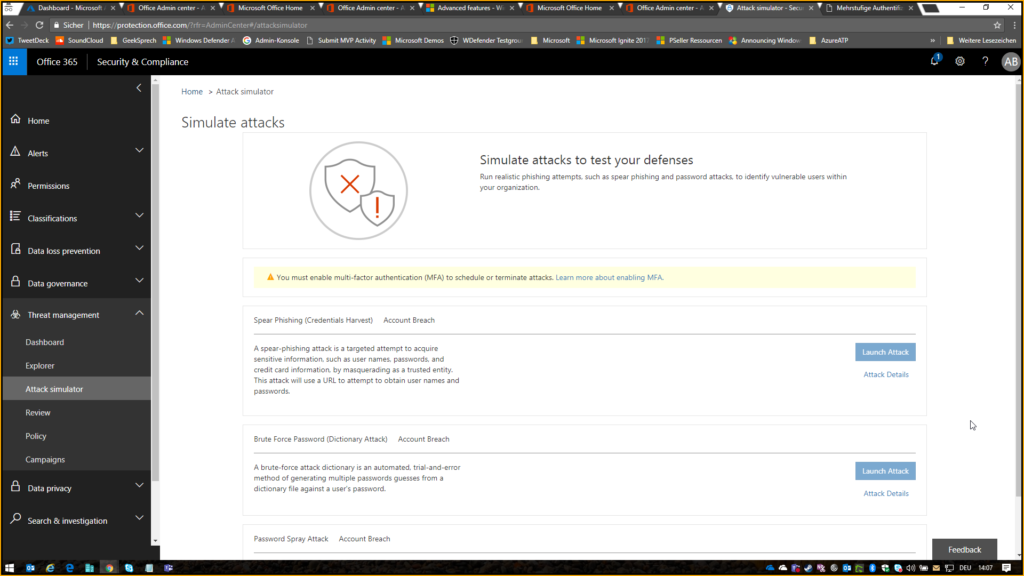
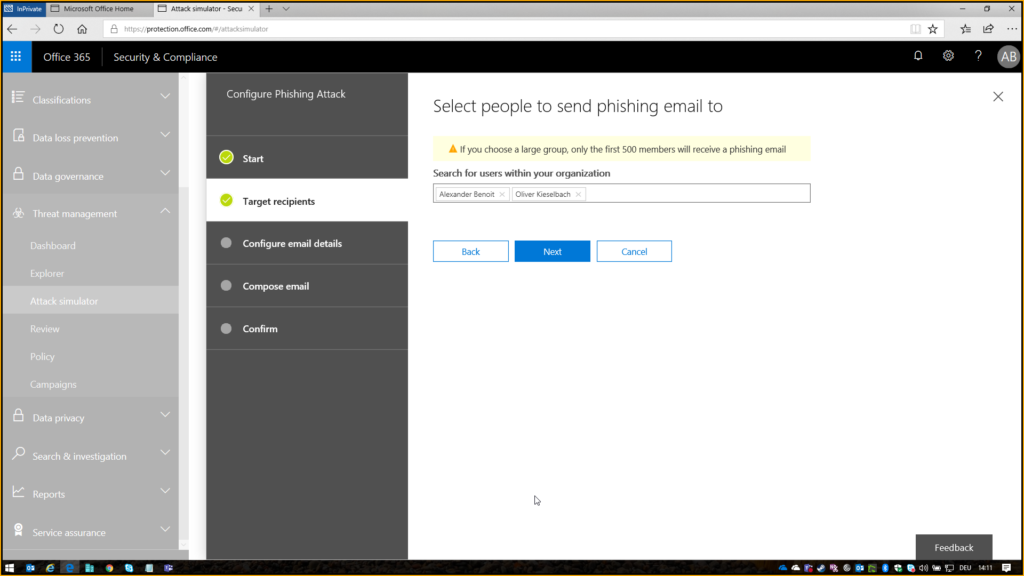
Give it a random name and select the people / employees / users you want to attack:
In my example I decided to take a email from Microsoft Online Services Team as my template where I entered everything exactly the same way as you would find it if you get a mail from the services. The only thing that is different is the phishing login server url where the user will get guided to. Here you can choose from a list of available URL’s.
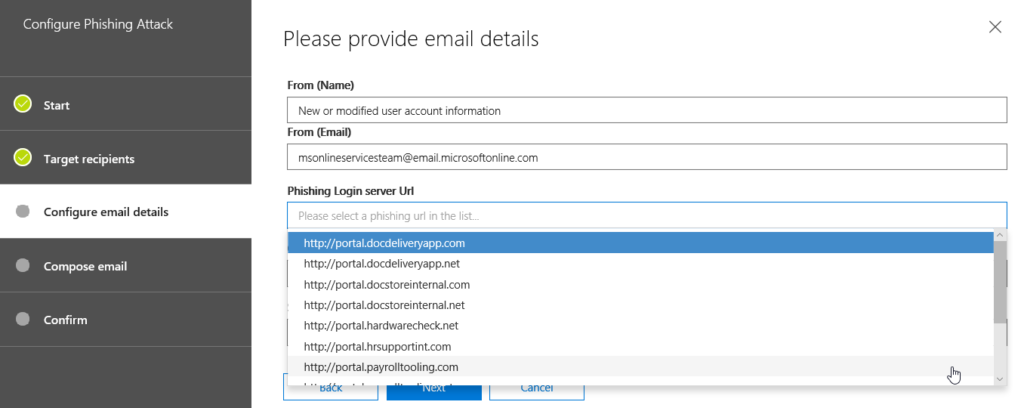
Configure one that fits best to your phishing attack. I chose the hrsupportint, because I faked an information email that normally gets send by Office365 adminportal when your account was modified.
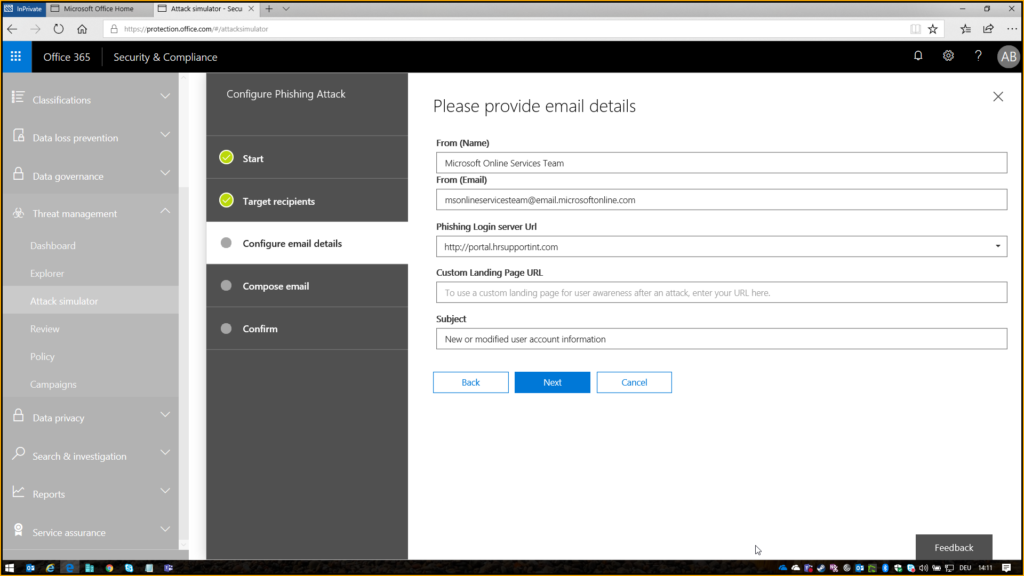
I copy and pasted the body from the “template” and replaced the loginpage with my variable

In addition I added the user name variable behind user name and wrote a random temporary password below. In our scenario it doesn’t matter what the user writes into the fields. The phishing attack will be successfull if the user clicks on the link.
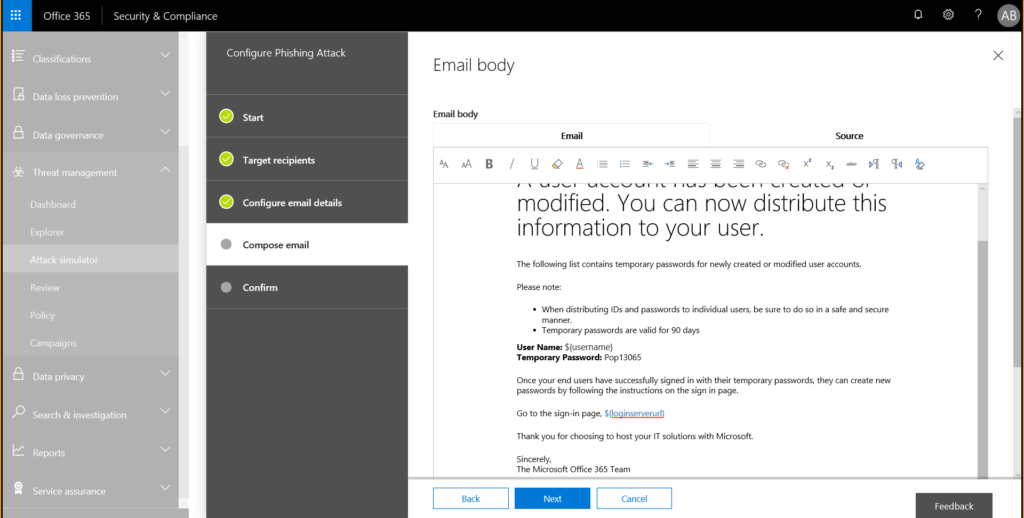
Confirm that you want to send it

The user will immediately receive the mail and if he clicks on the link the spear phisihing attack was already successful.
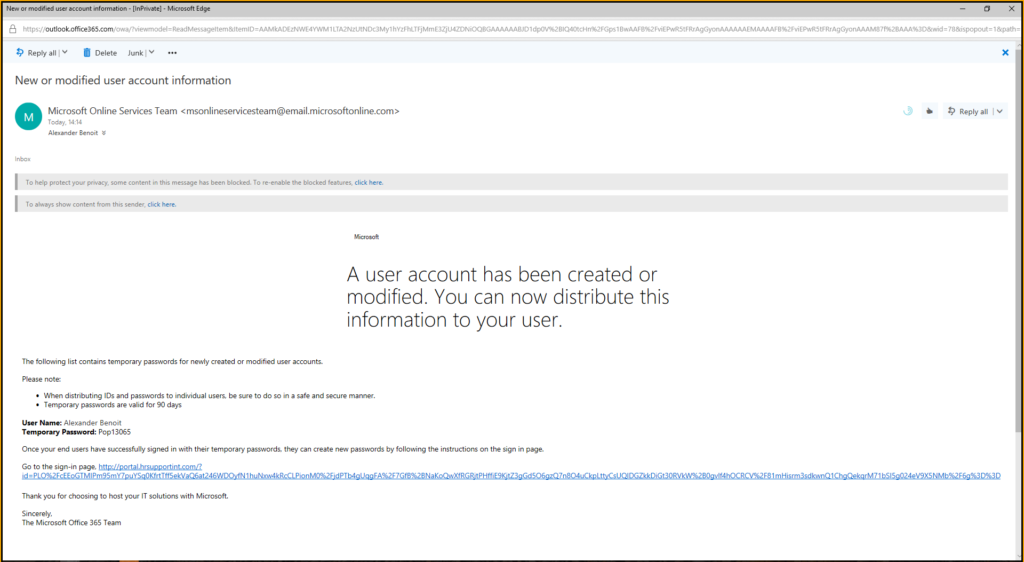
he will be redirected to a common login page which is exactly the same besides the url. He then will enter his login credentials

after his logon he will then receive the below message

while you as an admin will get the following report

Thats it.
The third part of this series will be a brute force password attack or dictionary attack that is an automated, trial-and-error method of generating multiple passwords guesses from a dictionary file against a user’s password.
Cheers
Captain

Submit a comment on “Attack Simulator for Office 365 Threat Intelligence – Spear Phishing Attack”