Pirate,
the third attack simulation method is a password spray attack. In a password-spray attack, a hacker tests a single password against multiple user accounts at an organization. The method often involves weak passwords, such as Winter2018 or Password123!, and can be an effective hacking technique against organizations that are using single sign-on (SSO) and federated authentication protocols, but that haven’t deployed multi factor authentication.
This is the last part of the Attack Simulator for Office 365 Threat Intelligence series:
- Attack Simulator for Office 365 Threat Intelligence – Overview and Preparation
- Attack Simulator for Office 365 Threat Intelligence – Spear Phishing attack
- Attack Simulator for Office 365 Threat Intelligence – Brute Force Password
- Attack Simulator for Office 365 Threat Intelligence – Password Spray Attack
Password spray attacks are pretty effective and really hard to detect. If you have Azure Active Directory in place I highly recommend an article of Alex Simons (Director of Program Management, Microsoft Identity Division) about Azure AD and ADFS best practices: Defending against password spray attacks. Within this article he describes four easy steps to disrupt password spray attacks.
To launch a passwords spray attack against your environment you need to navigate to https://protection.office.com/ and click on Threat Management > Attack Simulator > Launch Atack
Give it a random name…
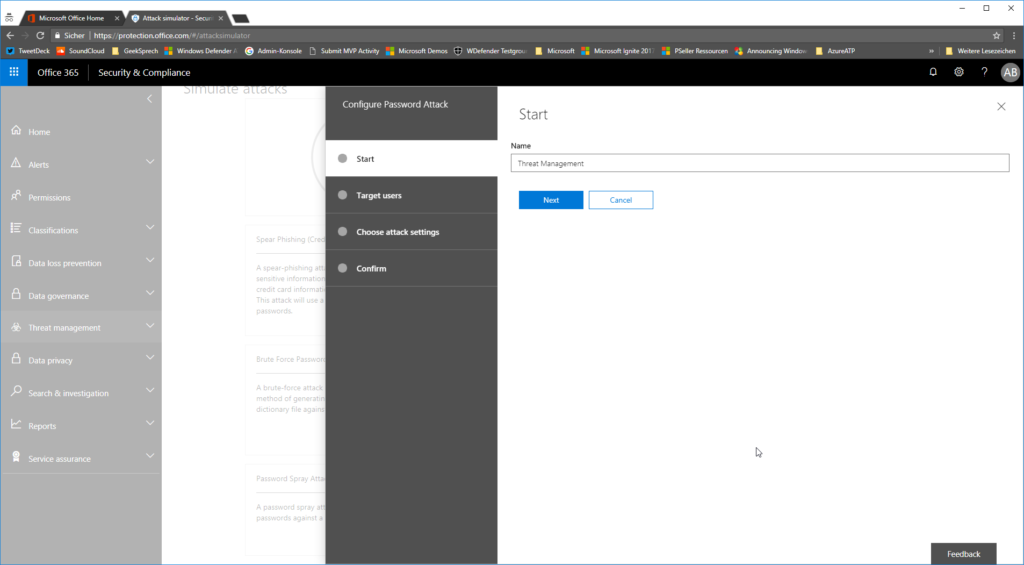
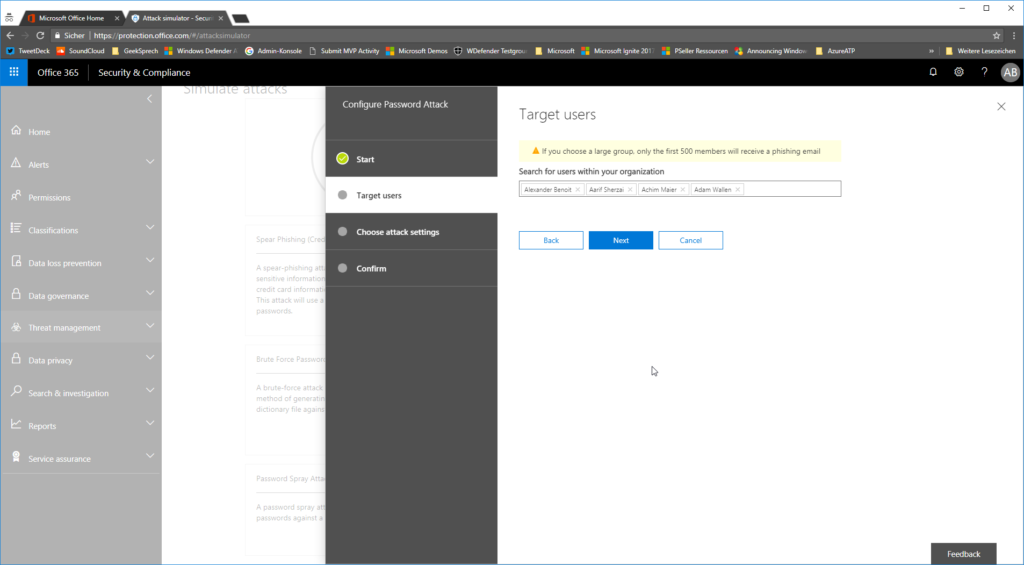
…and select the people / employees / users you want to attack:
Type in the password you want to spray
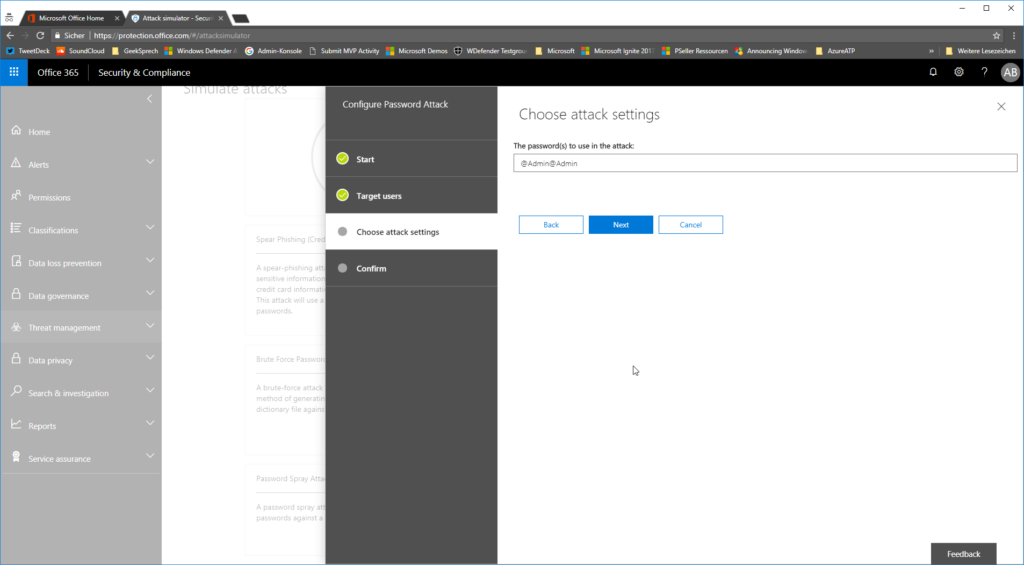
…and confirm that you want to launch that attack.
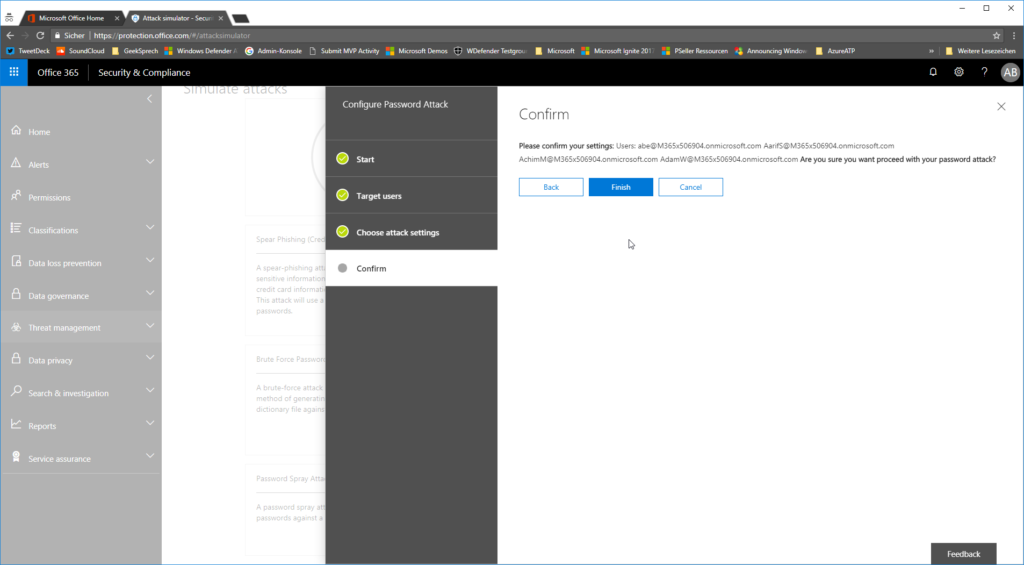
depending on the amount of users that you want to attack, it can take up to several minutes.
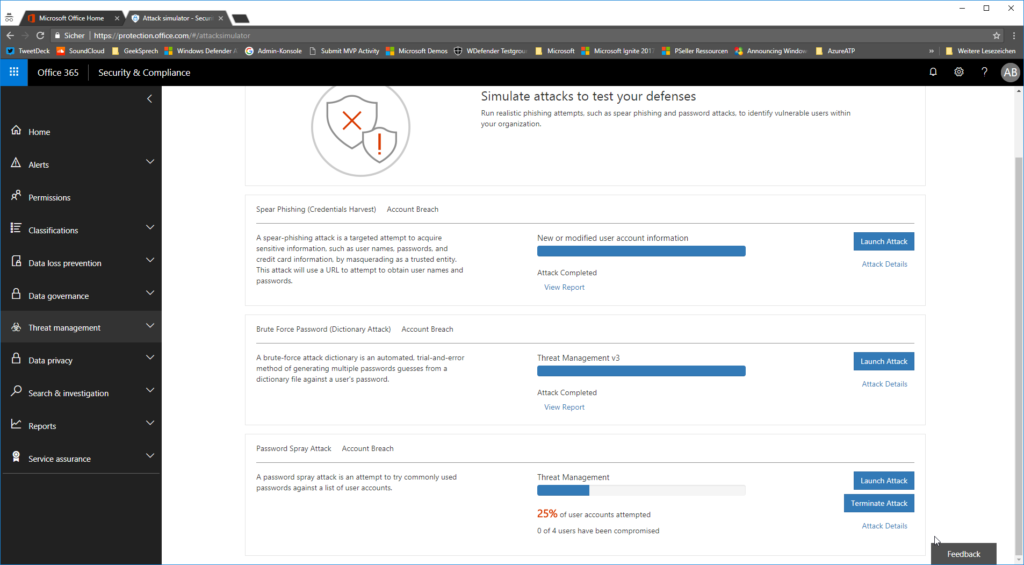
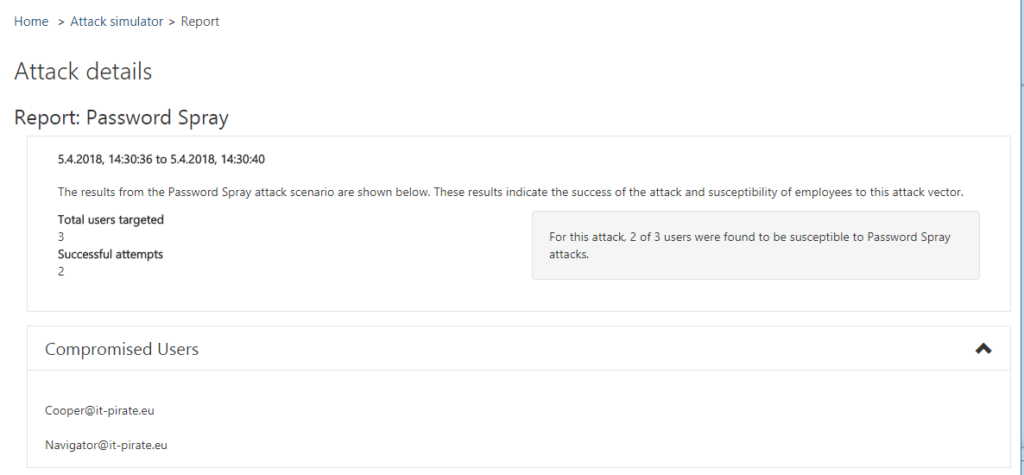
as soon as the attack is done you can review the attack details in the report
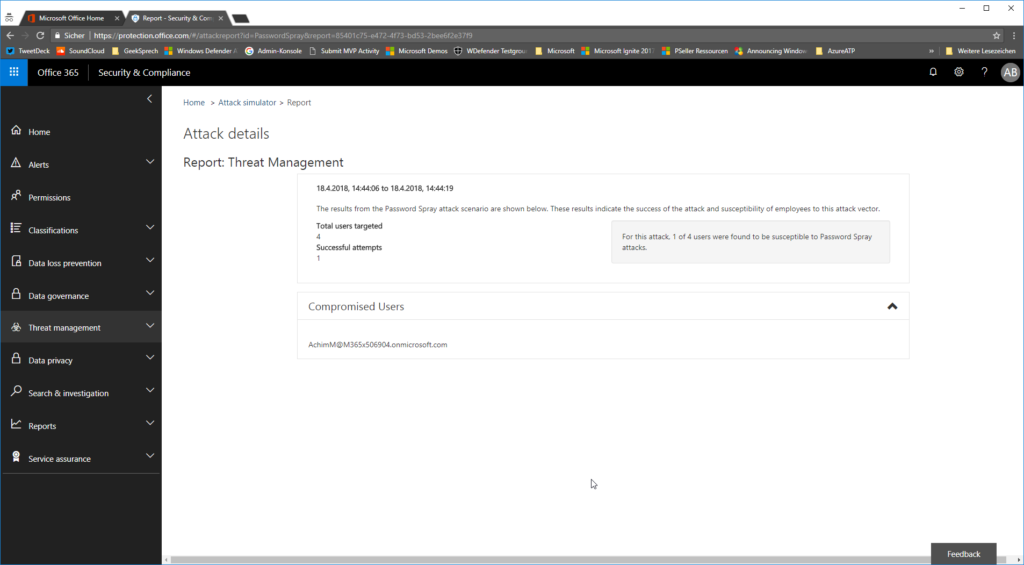
as a result you will get the users that have the password set.
Have fun!
*Cpt

Submit a comment on “Attack Simulator for Office 365 Threat Intelligence – Password Spray Attack”