Pirate,
Email spam is once again the most popular choice for sending out malware. Spam has been one of the main infection vectors for decades. During the past few years, it’s gained more popularity against other vectors, as systems are getting more secure against software exploits and vulnerabilities. A recent report of F-Secure reports that spam email click rates have gone up from the 13.4% recorded in the second half of 2017 to 14.2% recorded in the first half of the year. To protect against these attack vectors is nearly impossible as a majority of attacks leads to web pages never seen before and due to the the sheer infinite range of these attack vectors. The only thing that really improves our security level is permanent education of our users.
On 02-21-2018 Microsoft has announced the Public Preview of Attack Simulator for Office 365 Threat Intelligence. In preparation of some customer workshops I had a first look into the product that I want to share with you.
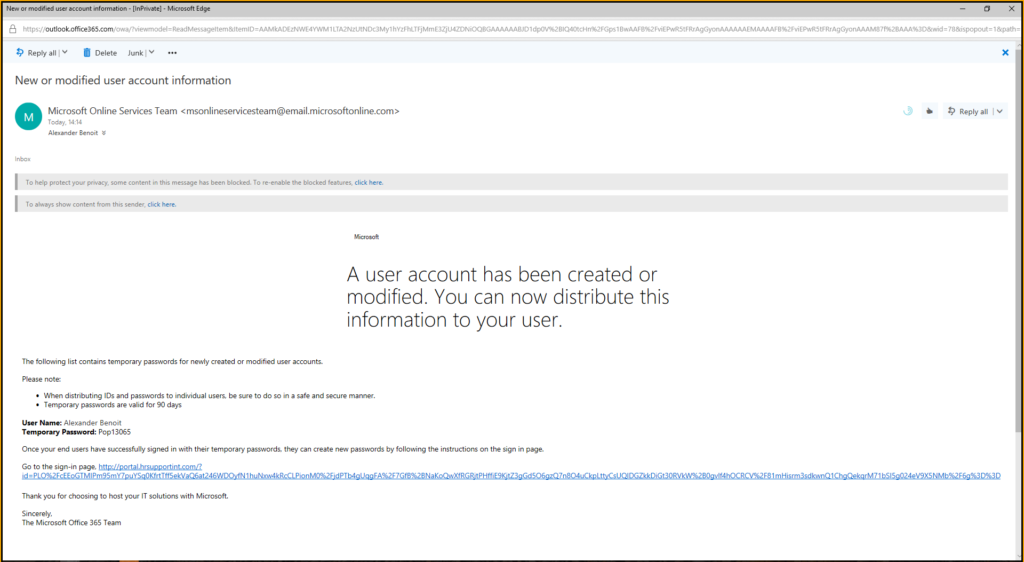
This is the first part of the Attack Simulator for Office 365 Threat Intelligence series:
- Attack Simulator for Office 365 Threat Intelligence – Overview and Preparation
- Attack Simulator for Office 365 Threat Intelligence – Spear Phishing attack
- Attack Simulator for Office 365 Threat Intelligence – Brute Force Password
- Attack Simulator for Office 365 Threat Intelligence – Password Spray Attack
In April 2017 Microsoft released Threat Intelligence as a tool to help organizations become more proactive with their cybersecurity. Therewith we got all the cool stuff around:
- Interactive tools to analyze prevalence and severity of threats in near real-time.
- Real-time and customizable threat alert notifications.
- Remediation capabilities for suspicious content
- Expansion of Management API to include threat details—enabling integration with SIEM solutions.
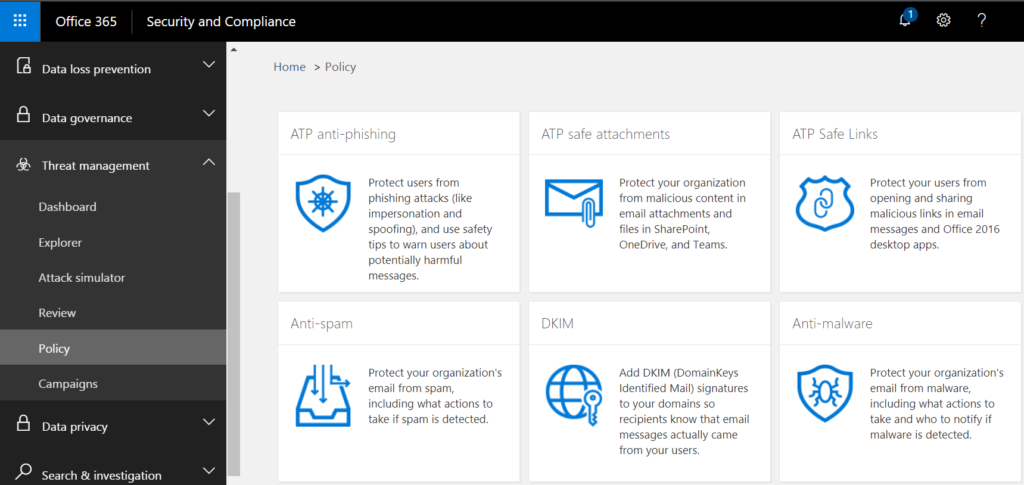
Attack simulator now comes in addition and is a perfect supplement to prevent the impact from threats before any security is required. With Attack Simulator, admins can launch attacks on their users, and find out more about the users behaviour.
Attack Simulator today includes three attack scenarios:
Spear Phishing (Credentials Harvest)
A spear-phishing attack is a targeted attempt to acquire sensitive information, such as user names, passwords, and credit card information, by masquerading as a trusted entity. This attack will use a URL to attempt to obtain user names and passwords.
–> it’s part two of this series
Brute Force Password (Dictionary Attack)
A brute-force attack dictionary is an automated, trial-and-error method of generating multiple passwords guesses from a dictionary file against a user’s password.
Password Spray Attack
A password spray attack is an attempt to try commonly used passwords against a list of user accounts.
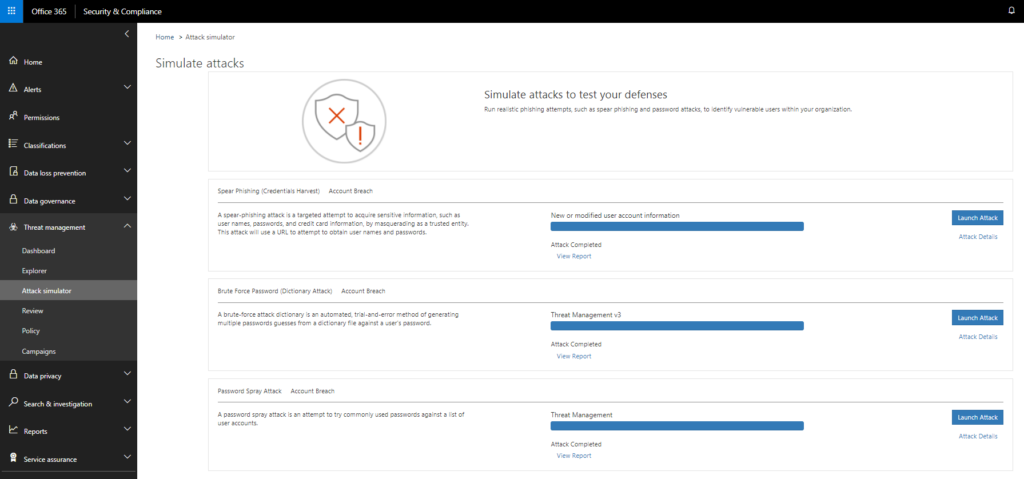
Preparation and Requirements
Good to know: Office 365 Threat Intelligence is available in Office 365 Enterprise E5. If your organization is using another Office 365 Enterprise subscription, Office 365 Threat Intelligence can be purchased as an add-on.
First of assign the licences, then you need to enable the feature in Security and Compliance portal:
https://protection.office.com/
Navigate to Threat Management > Attack Simulator
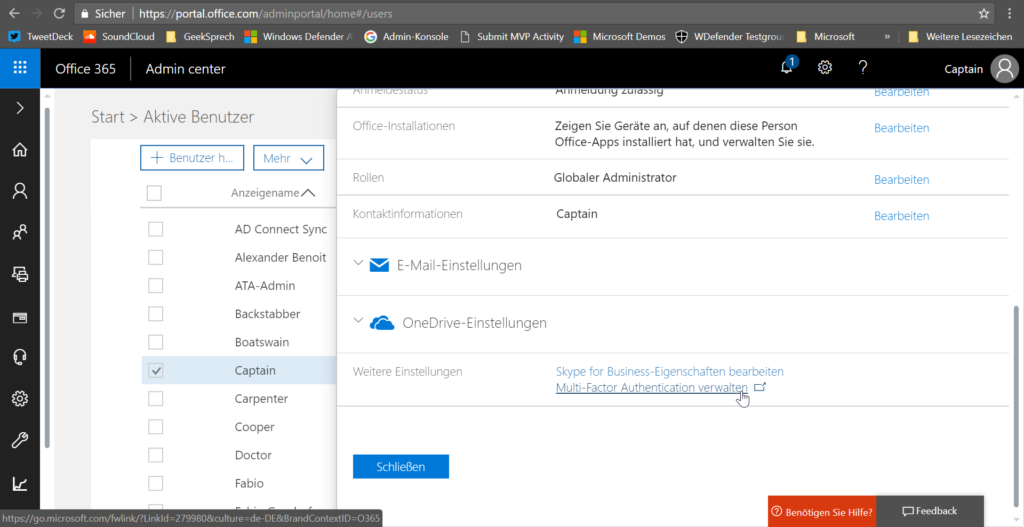
At least the user who runs the attack simulation needs to have Multi-Factor Authentication activated 😉
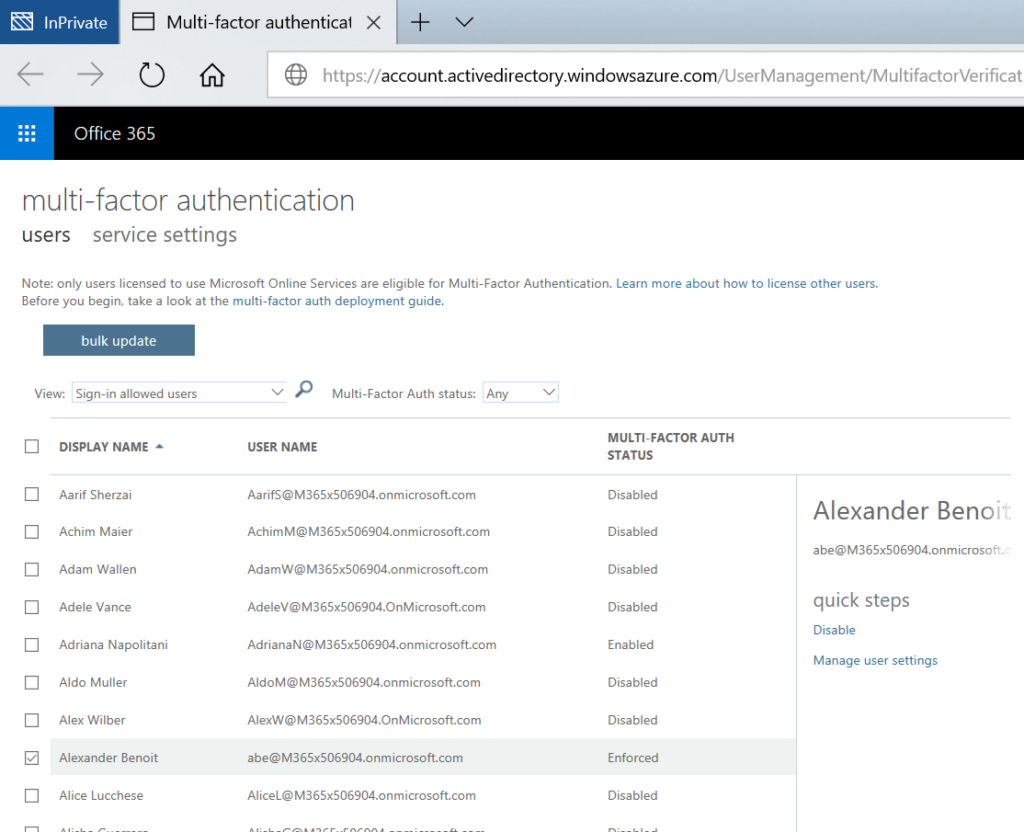
Go to https://portal.office.com/adminportal/home#/users select the user account or your admin account. Scroll down and click on Multi-Factor Authentication:
You will then get forwarded to the MFA configuration portal. Here you need to set the MFA status to enforced
At the next login to portal.office.com you will be asked to set up multi factor authentication. Click on “set it up now”

Chose what ever authentication method is comfortable for you. I will go with the mobile app


Now you need to open the app and add another account. Select Work or school account and scan the barcode.

You then need to set up an additional security verification method in case your prefered one isn’t available.


Now you are all set.
In the next part we will have a look into Spear Phishing (Credentials Harvest) attack.
Sail Ho!
*Cpt

Submit a comment on “Attack Simulator for Office 365 Threat Intelligence – Overview and Preparation”