Pirate,
The current Windows 10 Insider Build 16257 includes upcoming features of Redstone 3 and Windows 10 1709. Also included are all the features of the Windows Defender Application Guard (WDAG). The feature will work like a sandbox. The feature is intended to prevent malicious content and downloaded files from harming the system. After surfing, the isolated tab closes and clears all malicious code together with the temporary container. Admins can already create Whitelists from harmless pages that start in conventional Edge windows. Pages not listed then open in an application guard container within Edge.

Windows Insider Build 16257 has done quite a bit in Windows Defender Application Guard.
First things first…
Hardware Requirements:
Be sure you’ve got Windows Enterprise installed and your hardware supports the following:
- 64-bit OS for VBS (like Credential Guard)
- CPU with minimum 4 cores virtualization extensions (for Virtualization)
- 8GB Hardware memory (minimum!)
Additional information can be found here
Installing Windows Defender Application Guard
WDAG can be enabled using the Windows Features wizard on the target system.
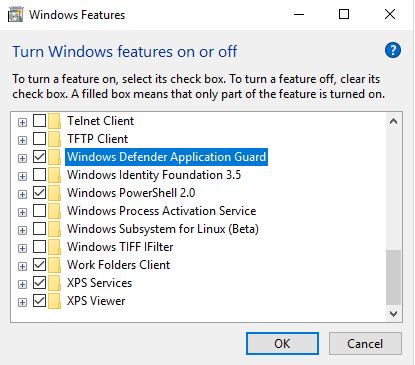
This can be done through PowerShell as well:
Enable-WindowsOptionalFeature -online -FeatureName Windows-Defender-ApplicationGuard
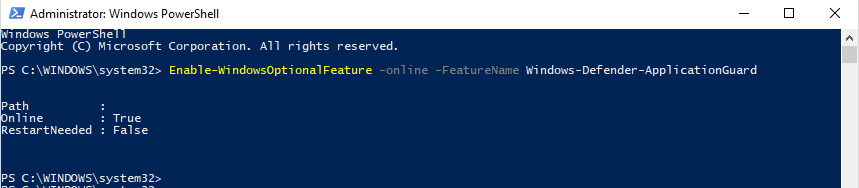
Afterwards, a restart of your client is needed.
Now we can manually open new instances of Application Guard from Edge:
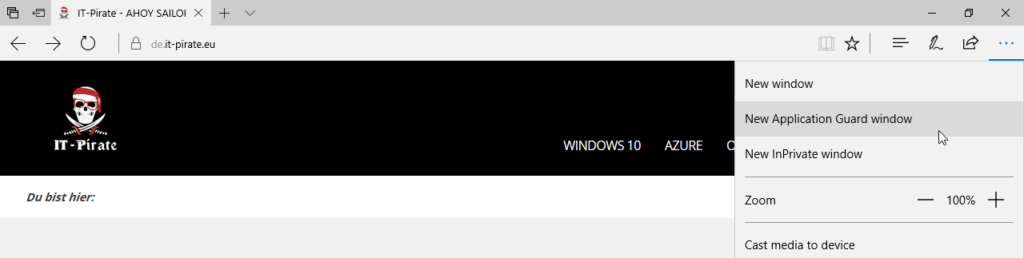
At startup, the isolated environment gets initiated.
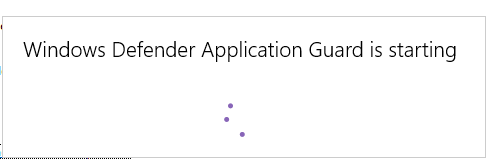
Then we get an Edge window with the indication that we’ve opened an ApplicationGuard isolated environment.

If you can not select “New Application Guard Window” in the context window, check again whether you meet the software and hardware requirements.
Configuration of the trustworthy pages
As mentioned above, however, the concept of Application Guard is different, because it follows a whitelisting procedure. In the Group Policy Management Editor, go to “Enterprise resource domains hosted in the cloud” under:
Computer Configuration \ Administrative Templates \ Network \ Network Isolation
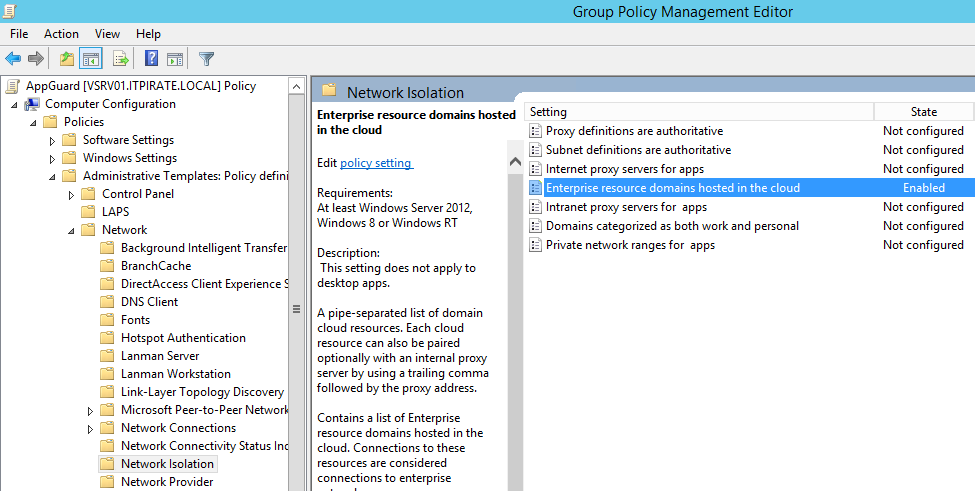
You have to add the pages which are trustworthy and should not be opened in a Windows Defender Application Guard window. The domains must be specified with point (.) And separated with pipe (|):
.it-pirate.eu|.geeksprech.de
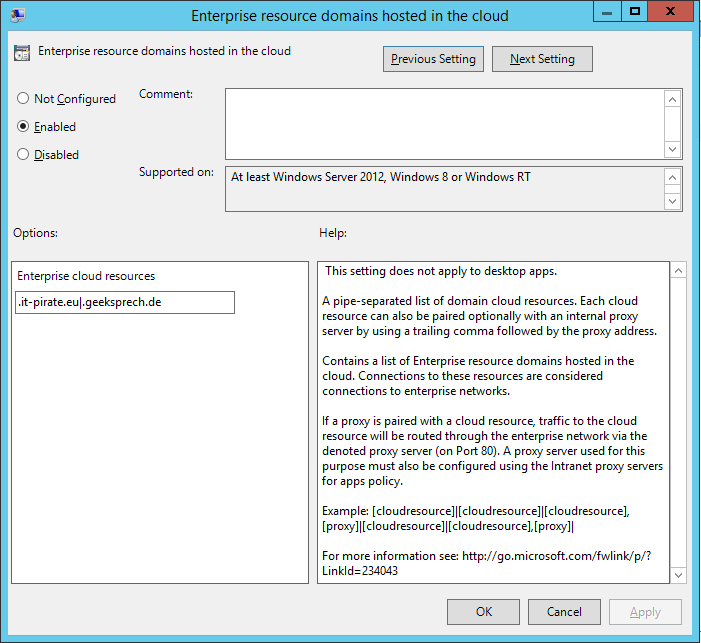
Now you must configure that the defined pages should be pulled and used with WDAG.
With the Creators Update or Windows 10 1703 we have received the appropriate policies through ADMX to enable Windows Defender Application Guard. As always, there is the possibility to activate WDAG via Group Policy:
Computer Configuration \ Administrative Templates \ Windows Components \ Windows Defender Application Guard
The “Turn On / Off Windows Defender Application Guard (WDAG)” policy must be activated
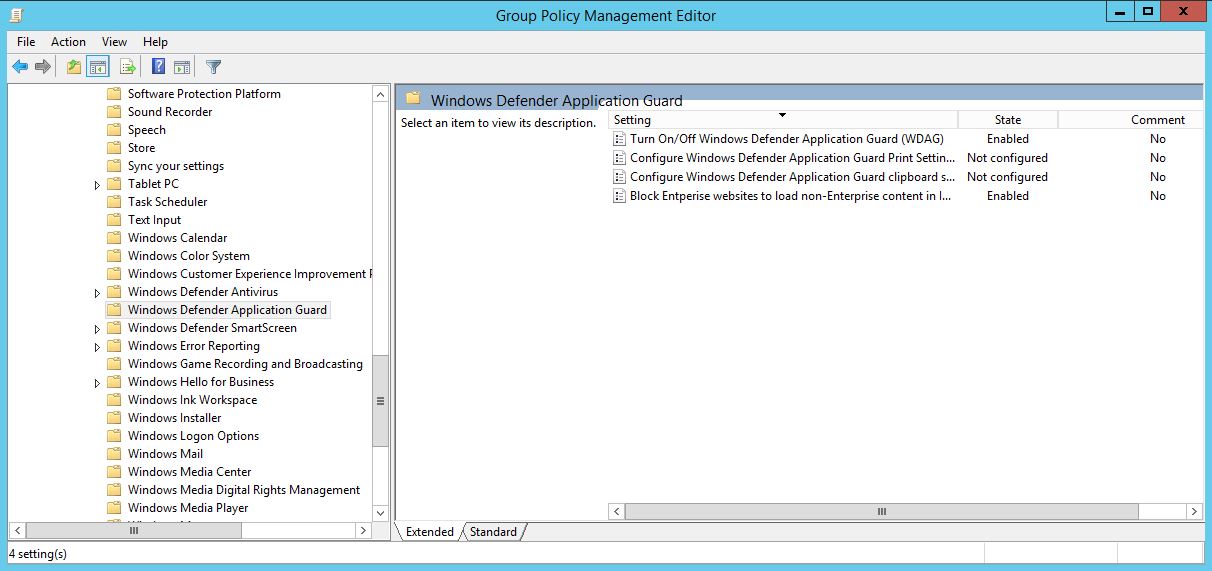
but as long as WDAG isn’t relased I suggest to configure everything through “Local Group Policy Editor”:
Computer Configuration \ Administrative Templates \Windows Components \ Windows Defender Application Guard
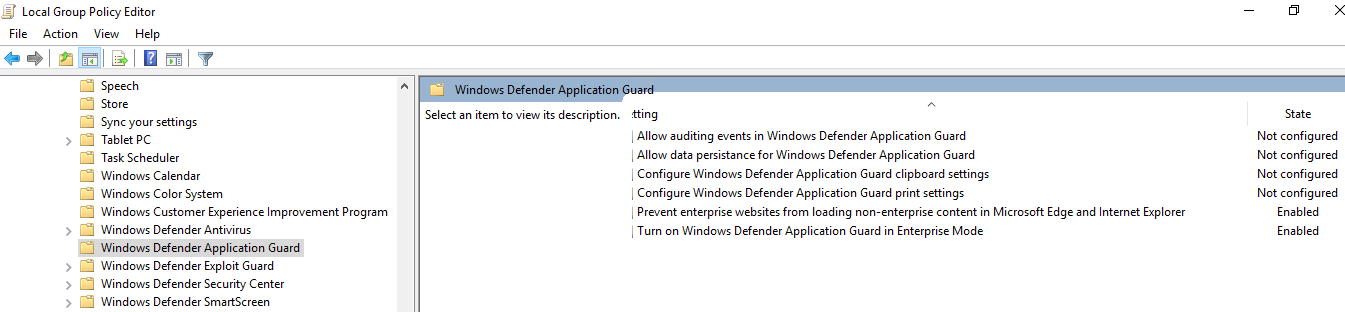
Registry is another way to configure:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\AppHVSI
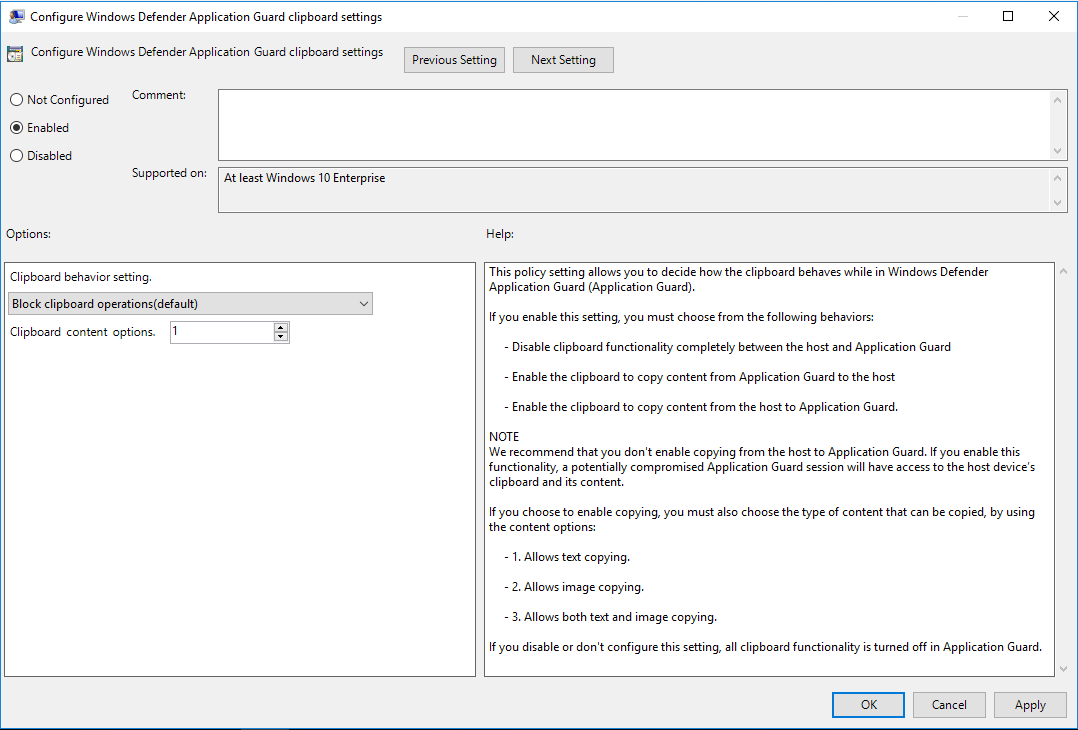
You can configure how to handle clipboard settings
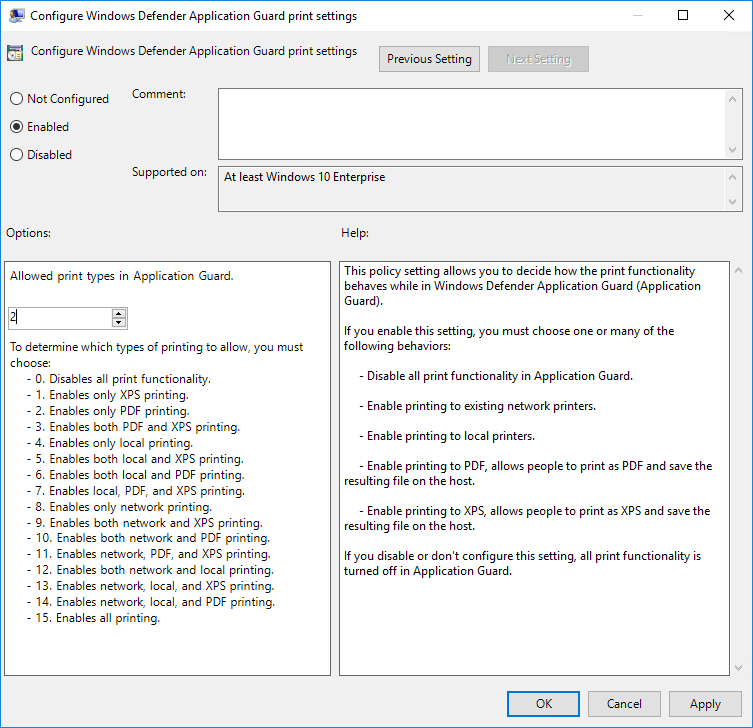
and it’s possible to configure printer settings
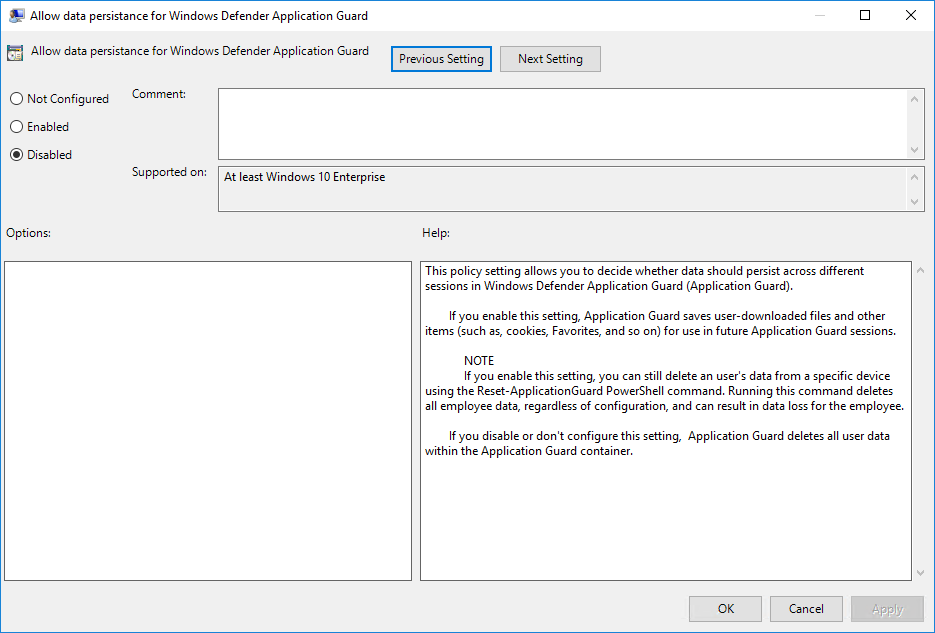
With one of the last builds we also received a way to handle downloaded files within an Application Guard silo.
It is possible to include events in the event log that were created in a Windows Defender Application Guard containers.
Since Windows 10 Insider Preview Build 16257 there’s an additional option to optimize the start behaviour by not suspending the container:
Added a registry key to allow users to optimize WDAG launch times during active browsing by not suspending the WDAG container when the WDAG window is closed. You can set the registry key to optimize for performance here: Computer\HKLM\Software\Microsoft\HVSI\, Value name: SuspendOnContainerClosed, REG_DWORD, Value data: 1. Note: Setting this key will result in the container not pausing and the container will not release committed memory.
Cheers
*Captain
Sources:
Announcing Windows 10 Insider Preview Build 16257 for PC & Build 15237 for Mobile
Windows Defender Application Guard Standalone mode
Neue Windows-10-Version zeigt ‘Application Guard’
Testing scenarios using Windows Defender Application Guard in your business or organization
Frequently asked questions – Windows Defender Application Guard

Submit a comment on “Windows 10 – Configure Windows Defender Application Guard for Microsoft Edge”