Microsoft Purview: Endpoint DLP Part 2
In the previous article on Endpoint DLP, I presented the basic functionality of Endpoint DLP with real life examples.
In this blog post, I will now go into more depth of the different features.
I present the individual protection options with examples and screenshots.
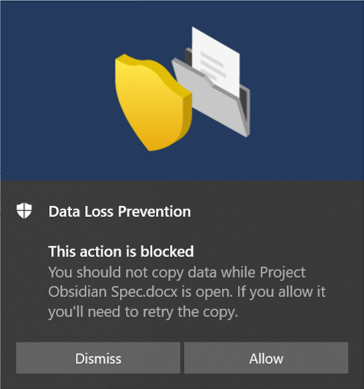
Use case:
A member of the supervisory board, Dr. Ludwig K., works with sensitive data of level C-4.
C-4 is the most sensitive data and any leakage can severely harm the enterprise.The naming could be different in other companies or enterprises, but the bottom line is, everything boils down to “strictly confidential”.