Meet Frank P. He is a project manager in the development department of a medium-sized automotive company.

He is under a lot of pressure and has a deadline to meet to file a patent.
After a 14-hour workday, he sends the final version of his draft patent to his patent attorney on Friday evening. Outlook completes the e-mail address and Frank presses the “send” button. Satisfied, he shuts down the laptop and looks forward to the weekend…
…only to discover the following Monday that the email went to someone else. He is lucky because the recipient is a good business partner who deletes the document.
As CFO, Ulrike B. is responsible for the entire finances of a DAX company.

In the evening at home, she uploads a series of Excel spreadsheets to SharePoint Online to work on them collaboratively with colleagues. Unfortunately, she makes a mistake during the upload. She marks one file too many. Of all things, the list of highly confidential data about a company acquisition is also in the selection and is uploaded by mistake.
Meet Carsten K. He has quit his job as a team leader in sales at a global shipping company after clashing violently and repeatedly with his superiors.

He already has a new position with the competition and wants to take his customer master data with him as a basis for his work. He has already exported the customer data from CRM to a large Excel file. However, Microsoft Purview has classified it as “Confidential” based on recognition algorithms without his knowledge. On his last day at the office, he wants to upload the file to his private DropBox.
All three cases are taken from real life as examples.
Data loss can happen to any employee at any time, both accidentally and intentionally.
In these three cases, Microsoft Purview Data Loss Prevention (formerly Office 365 Data Loss Prevention) can prevent it.
Case 1:
In the first case, a mail flow rule in Exchange Online can block the email. Alternatively, with the help of the AIP client and a custom configuration, the email can be blocked in Outlook before it is sent.
Case 2:
Since the DAX company uses Microsoft Defender for Cloud and Office365 is connected via a connector, the accidental upload can be controlled and blocked.
Alternatively, Endpoint DLP can already prevent the upload via the browser.
Case 3:
The private DropBox is not connected to Defender for Cloud. Therefore, only Endpoint DLP can help here.
This blog post is about Microsoft’s Endpoint DLP functionality and introduces Endpoint DLP with the help of the third example case. It will not go into every detail, if there is a need for that, then please give me feedback.
What is Endpoint DLP anyway and why do we need it?
- Endpoint Data Loss Prevention (Endpoint DLP) is part of the Microsoft Purview Data Loss Prevention (DLP) suite of features that can be used to detect and protect sensitive items across Microsoft 365 services and has been publicly available for 1 ½ years.
- It can prevent and audit accidental or intentional data leaks on “endpoints” (Windows & macOS)
- All preconfigured or self-created DLP types for sensitive information (credit card numbers, ID card numbers, …) or sensitivity labels that have already been set up in the Purview portal can be used as triggers for a DLP policy.
- It uses the blocking technology from Microsoft Defender for Endpoint to prevent data loss.
The history
The History
In the past, data loss from endpoints such as Windows 10 machines, Android and iOS could only be prevented with the help of Windows Information Protection.
However, these had to be managed by Device Management such as SCCM or Intune. The protection mechanisms were configured in the respective device management portal and deployed to the end devices. In order to prevent the loss of files with AIP sensitivity label, one would also need a configuration in the corresponding label in the Compliance Portal. This then had a connection established via Azure to the device managements.
In mid-April 2020, this connection was capped.
Customers who used this feature had the opportunity to enroll in the private preview of Endpoint DLP – then referred to by the project name Delphi. In November, Endpoint DLP left private preview status and was publicly announced and made available.
What does Endpoint DLP include?
As described above, Endpoint DLP can be used to prevent data loss from “endpoints”.
“Endpoints” in this context are Windows 10 / 11 and MacOS machines. For mobile devices based on Android or iOS, App Protection Policies in SCCM or Intune (Endpoint Management) are still required.
Using one of the above examples, I present here how Endpoint DLP works. Finally, there is a subjective overview of the advantages and disadvantages of Endpoint DLP.
In the appendix you will find the currently valid – as of May 2022 – technical data.
Functionalities
| Activity | Description | Windows 10/11 | MacOS Catalina |
| Upload to a cloud service or access through unauthorized browsers | Detects when a user attempts to upload an item to a restricted service domain or access an item through a browser. If the user is using a browser that is listed as a disallowed browser in the DLP list, the upload activity is blocked, and the user is redirected to use Microsoft Edge. Microsoft Edge then allows, or blocks upload or access based on the DLP policy configuration | Yes | Yes |
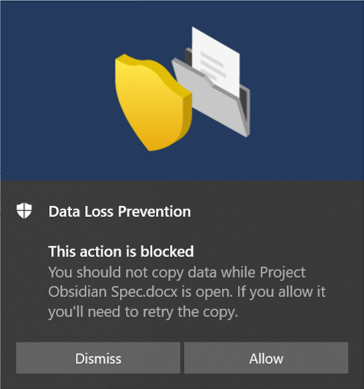
| copy to another application / clipboard Share with another application | Detects when a user attempts to copy information from a protected item and then paste it into another application, process, or item. Copying and pasting information within the same application, process or item is not recognized by this activity. Detects when another application should be used to share the protected element. | Yes | Yes |
| Copy to USB removable disk | Detects when a user tries to copy an object or information to a removable disk or USB device. | Yes | Yes |
| Copy to a network share | Detects when a user attempts to copy an item to a network share or mapped network drive | Yes | Yes |
| Print a document | Detects when a user attempts to print a protected object on a local or network printer. | Yes | Yes |
| copy to a remote session | Detects when a user tries to copy an item to a remote desktop session | Yes | No |
| Copy to a Bluetooth device | Detects when a user attempts to copy an object to an unauthorized Bluetooth app (as defined in the list of unauthorized Bluetooth apps in the Endpoint DLP settings). | Yes | No |
| Create a file | Detects when a user creates a file | Yes | No |
| Rename a file | Detects when a user renames a file | Yes | No |
In our “Case 3”, these are the activities “Upload to a cloud service or access through unauthorized browsers” .
This comes into play when Carsten K. uses his web browser and logs into his private account on dropbox.com.
In case he has the Dropbox synchronization client on the computer, then the activity “copy to another application” is the appropriate one. Copy is used here synonymously with upload.
The first and most important basis to know is that Endpoint DLP works only on captured or registered devices.
This has the following background: Endpoint DLP (abbreviated eDLP from here on) enforces its policies through Microsoft Defender for Endpoint. Defender does not have to be the primary antivirus but can run in passive mode alongside other protection software. The prerequisite is that Defender is installed.
Further software installation is not necessary.
Onboarding into eDLP can be done in various ways, through a local script, via Group Policy, SCCM, Microsoft Manager for Endpoint (Intune) or even VDI onboarding scripts for non-persistent machines.
After this is done and the first data arrives in the Purview Portal in the Activity Explorer, you can continue in different ways.
I’ll first go into the boundary conditions that you need to create. These are a combination of the endpoint DLP settings and the policy that applies them.
The Endpoint DLP Settings are global settings. These include, for example, applications that are to be controlled. Or a URL positive or negative list.
The list of currently possible publicly available settings is as follows:
| Setting | Windows 10, 1809 and higher, Windows 11 | macOS Catalina 10.15 or higher | Notes |
| File path exclusion | Supported | Supported | macOS includes a recommended list of exclusions that are enabled by default. |
| Restricted apps | Supported | Supported | |
| Restricted app groups | Supported | Not supported | |
| Unapproved Bluetooth apps | Supported | Not supported | |
| Browser and domain restrictions for confidential files | Supported | Supported | |
| Additional settings for eDLP | Supported | Supported | Only the default justifications are supported for macOS devices. |
| Always monitor file activities for devices | Supported | Supported | |
| Automatic quarantine of unauthorized apps | Supported | Not supported | |
| Advanced classification | Supported | Not supported | |
| Justification in policy tips | Supported | Supported |
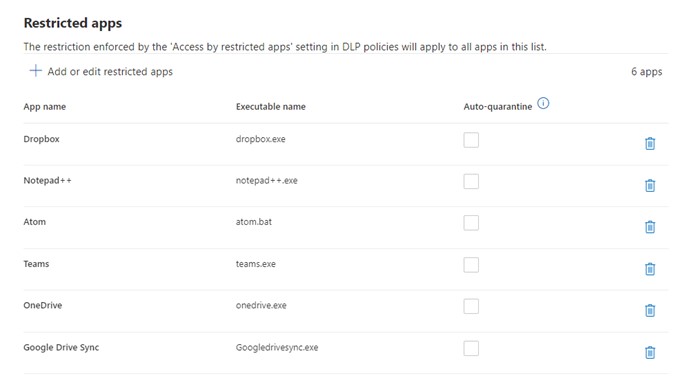
In our case of the disgruntled sales employee Carsten, we find the entry dropbox.exe among others in the “Restricted apps” setting.
As a result, interaction with the dropbox.exe process is controlled.
To prevent uploading via the DropBox client, the administrator then later selected the “Block” option in the policy under “Restricted app activities”.
In combination with
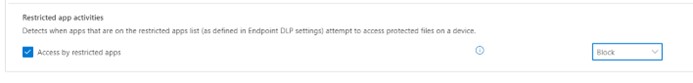
If Carsten K. now tries to upload the file via the browser, this is also controllable and thus preventable.
Uploading files via browser is also included in eDLP’s scope of services.
Once this is possible natively in the Microsoft Edge browser. In addition, one can distribute an extension for Google Chrome via various options such as Group Policy or Endpoint Manager (Intune).
Google Chrome must then be removed from the list of disallowed browsers.
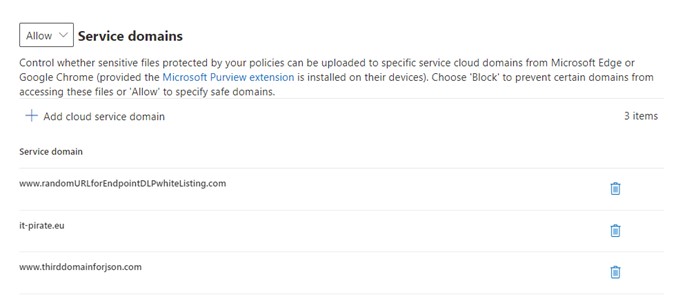
Now you have to decide which approach to choose: Positive or negative list.
In the positive list are the allowed URLs. That is, only these destinations on the Internet may be used for upload. Everything else is blocked.
The negative list approach first allows everything by default except for the URLs entered in the negative list.
In case 3 the company has decided to use a positive list. https://www.dropbox.com is not on this list and therefore Carsten K. cannot upload the file there either.
If no domain is enabled for uploading sensitive data, then you have to enter a dummy URL. See screenshot from our dev environment.
The general, global settings are not enough. As mentioned above, at least one policy must be created for the settings.
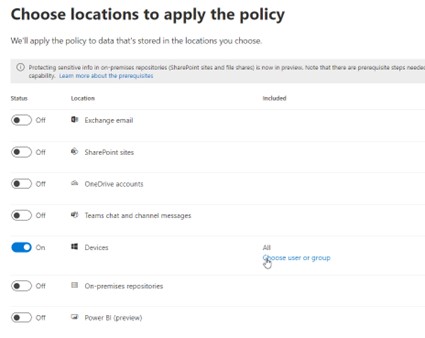
This defines the “scope” of eDLP.
The scope is specified in the wizard under “Devices”. Here you can select either individual persons or entire groups. In addition, it should be noted that the machines of these users are really enrolled.
Carsten K. and his whole sales team are enrolled and in the list of users.
Once this is decided and set, you create a rule within this policy.
As a rule, conditions are now defined which must be fulfilled for the DLP mechanism to take effect.
These can be file types, sensitivity labels or DLP detection algorithms. In addition, conditions can be nested and supplemented.
Furthermore, exceptions can be added to the conditions.
Example of our Case 3: The Sensitivity Label “Confidential” was automatically added to the file by Purview Data Loss Prevention after Purview detected customer data in the file. This was previously configured by the administrator.
Two conditions are possible here. Once, the detection mechanism that detected customer data in the file could be set as a trigger. Or alternatively the sensitivity label “Confidential” can be the trigger.
Then we have to tell Purview what to do when these conditions and exceptions are met: the Actions.
The actions are:
- Block
- Block with the possibility to “overwrite” the block
- Audit
In the case of Claus K., the actions in question are relevant to the browser/Internet activities and applications. Here it says “Block” both times
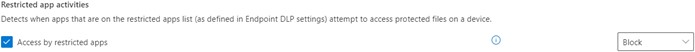

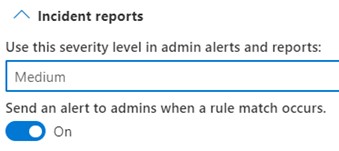
In addition, the admin has the option to trigger an alarm. This can be done in the system, or an e-mail is generated.
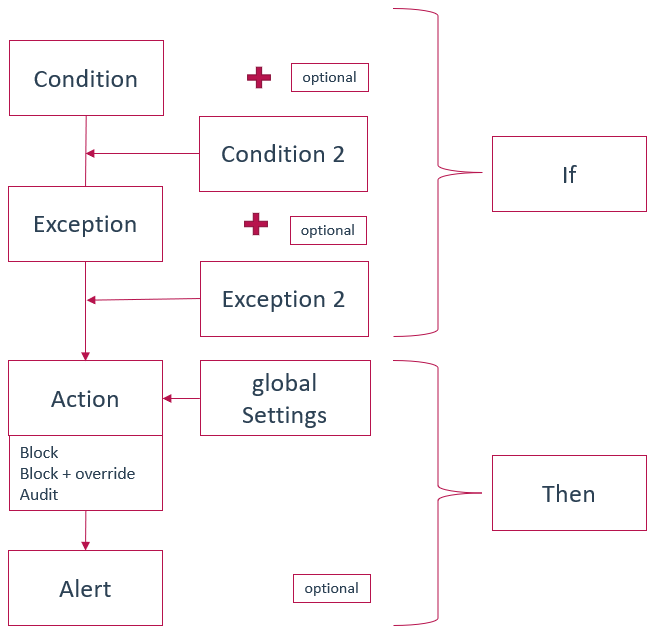
To summarize, the logic behind eDLP is:
- Global settings combined with rule in policy = protection.
- If – Then rule in the policy.
If condition is met (with optional exceptions),
Then the selected action is performed based on the global settings.
In our case 3 this would be:
IF = sensitivity label (or detection algorithm)THEN = block
Optional alert
The upload is blocked via the browser as well as via the Dropbox app, an alert is generated. Legal action could be taken.
Advantages and disadvantages:
Advantages:
- Endpoint DLP works cross-functionally with all Microsoft Purview / Information Protection solutions.
- eDLP closes the “DLP gap” on the endpoints
- Many features are already in private preview, the product is actively developed further
- Can be finely granulated and adapted to specific groups of people (via the policy)
- Users can be sensibilized/educated with the help of pop-ups
- No additional software installation is necessary
Disadvantages:
- All devices must be enrolled
- E5 License as a prerequisite means an investment that has to be justified (“Prevention is not sexy”)
- Small teething troubles, which are however gradually eliminated
Bottom Line
Of course, like all data loss prevention solutions, eDLP is not immune to individuals with high criminal energy.
If someone really wants to steal data, they will find ways and means to circumvent DLP.
The upload is blocked?
Then the monitor is photographed.
There will always be ways and means to circumvent protective mechanisms. See Microsoft Security Report 2021 – bell curve, “Protect Data”.
Nevertheless, eDLP covers the widest range of protection capabilities on endpoints, reliably and securely prevents data loss, and has become an important and indispensable building block in information protection.
I will go deeper into the details into the capabilities of Endpoint DLP in Part 2 of this blog post.
Thank you for your reading and have a great day.
Holger
Addendum
Supported file formats
Endpoint DLP supports monitoring of the file types in the list below. DLP checks the activities for these file types even if no policies are configured.
If permanent monitoring of activity for these file types is not desired or not allowed, then this can be disabled in the Endpoint DLP settings under the option “Always audit file activity for devices”.
However, this only affects Word, PowerPoint, Excel, PDF and .csv files.
All others are not monitored by default, but only if a corresponding policy has been created.
- Word files
- PowerPoint files
- Excel files
- PDF files
- .csv files
- .tsv files
- .txt files
- .rtf files
- .c files
- .class files
- .cpp files
- .cs files
- .h files
- .java files
About file types
File types are a grouping of file formats used to protect specific workflows or business areas. You can use one or more file types as conditions in your DLP policies. File types simplify the work of administrators by grouping file formats that logically belong together.
| File type | App | File extensions |
| Word processing | Word, PDF | .doc, .docx, .docm, .dot, .dotx, .dotm, .docb, .pdf |
| Spreadsheet | Excel, CSV, TSV | .xls, .xlsx, .xlt, .xlm, .xlsm, .xltx, .xltm, .xlsb, .xlw, .csv, .tsv |
| Presentations | PowerPoint | .ppt, .pptx, .pos, .pps, .pptm, .potx, .potm, .ppam, .ppsx |
| Archiving | Archive&Compression | .zip, .zipx, .rar, .7z, .tar, .gz |
| Outlook | .pst, .ost, .msg |
Good to know: Endpoint DLP captures all changes to file extensions or file names via the MIME protocols!
Other file formats
If the file types do not cover the file extensions to be used as a condition in a policy then you can use comma separated file extensions instead.
It should be noted that file types and other file formats cannot be used together in one policy. One must then switch to several policies.
Licensing
E5!
- Microsoft 365 E5
- Microsoft 365 A5 (EDU)
- Microsoft 365 E5 compliance
- Microsoft 365 A5 compliance
- Microsoft 365 E5 information protection and governance
- Microsoft 365 A5 information protection and governance
Further basic requirements can always be found in the Microsoft documentation or on the awesome website from Aaron Dinnage.

One pingback