At RSA 2019 I’ll be speaking about the Lost Boys: How Linux and Mac Intersect in a Windows-Centric Security World. We often see that Windows has such a large market share as the platform of choice, it can render Linux and Mac the Lost Boys in the world of security. This is also reinforced by the fact that the management of the two platforms for enterprise environments is simply not comparable to the administration of Windows client or server operating systems. But from the perspective of a security officer, this is as important as necessary. In November 2017, Microsoft announced that it will extend Windows Defender ATP partners across platforms. With that, the public availability of the WDATP integration of Ziften, Bitdefender and Lookout went live. With this comprehensive approach, Microsoft unites forces against cyber threats and adds lack of knowledge about behavior-based security solutions on these platforms through the industry expertise of its partners. This integration has now been extended to include two additional platforms, SentinelOne and Corrata. In this blog post I’ll give you a first introduction how the integration with Ziften can be done. Later we will have a look how the agent behaves on Mac and Linux machines with two different examples of real world attacks, that we have seen in the past couple of months.

3rd party integration
As in any other integration scenario you need to click on:
Settings > Onboarding > Linux, macOS, IOS and Android
to perform the onboarding. Here you can see the three publicly available onboarding methods Ziften, Bitdefender and SentinelOne. All three methods do have their own eco system in the backend which means that the sensors that you are going to install on the 3rd party OS will report in the backend of the three vendors. Through a push method all the data will then be forwarded through the WDATP API’s into the portal.
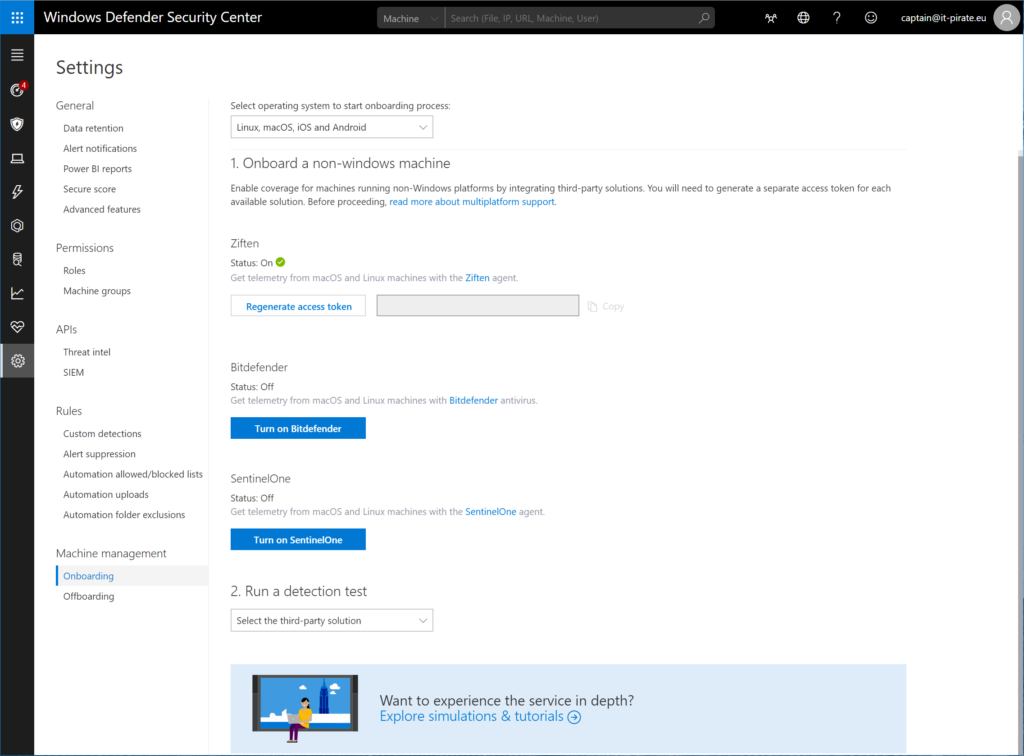
If you want to test the integration, all three vendors offer free trials. If you are interested click here:
After you created a trial tenant with one of the partners, you then need to turn on the integration

…and generate an access token:

This access token needs to be inserted into the 3rd party vendors connection interface:

…where you enter the previously in Windows Defender ATP generated access token:

Don’t forget to click the “UPDATE” button here.
After that you are done with the portal integration and can go ahead ahead with onboarding mac and / or linux machines. Each vendor provides dedicated agents which you need to download or deliver to the machines. After you have installed the agent I recommend you run the detection test, that you can find in the Windows Defender Security Center in the Settings > onboarding menu and run the following:
echo dGVzdD0vYmluL3NsZWVwO2NwIC9iaW4vc2xlZXAgL3RtcC9tYWxpY2lvdXNhdHRhY2tlcjsvdG1wL21hbGljaW91c2F0dGFja2VyIDU7cm0gL3RtcC9tYWxpY2lvdXNhdHRhY2tlciAK | base64 –decode | bash

Troubleshooting
There’s not much to troubleshoot in this scenario. If you ever have problems with machines you can compare the id’s between the both portals. In WDATP the machine ID is in the URL when you click on the machine ID.
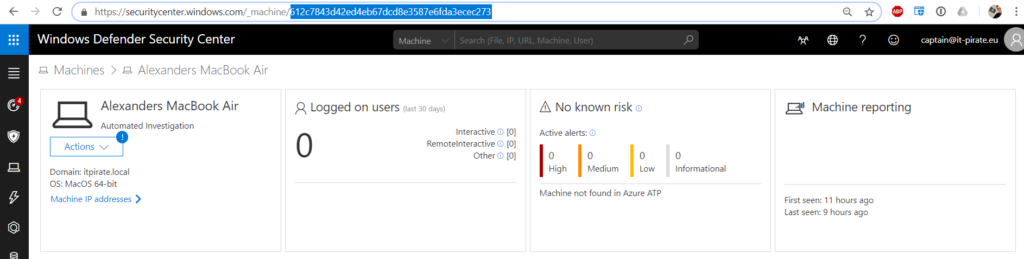
In Zenith you can find this information in Objects > Systems Here you need to select the machine you are looking for:

In the right pane of the system details there is line that says: “WDATP Machine ID“. This ID should be the same like one from WDATP above. If you need to contact support they will maybe ask you for this id.

Aaaaaaaaaaaaaaaaaaaaaaaaaargh
Captain

Submit a comment on “Windows Defender ATP: the lost boys – Mac & Linux”